Lab: Information Disclosure on Debug Page
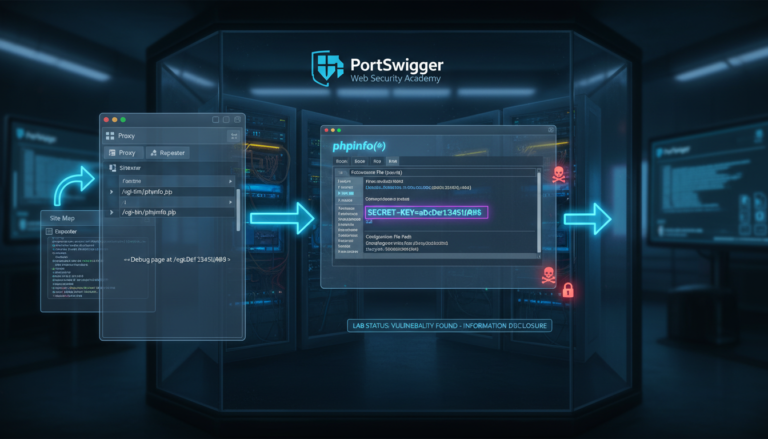
This lab demonstrates a common vulnerability where sensitive information is exposed through…

This lab demonstrates a common vulnerability where sensitive information is exposed through…

In the world of cybersecurity, the “Human Layer” remains the most targeted…

We are all familiar with the feeling: the to-do list never ends,…
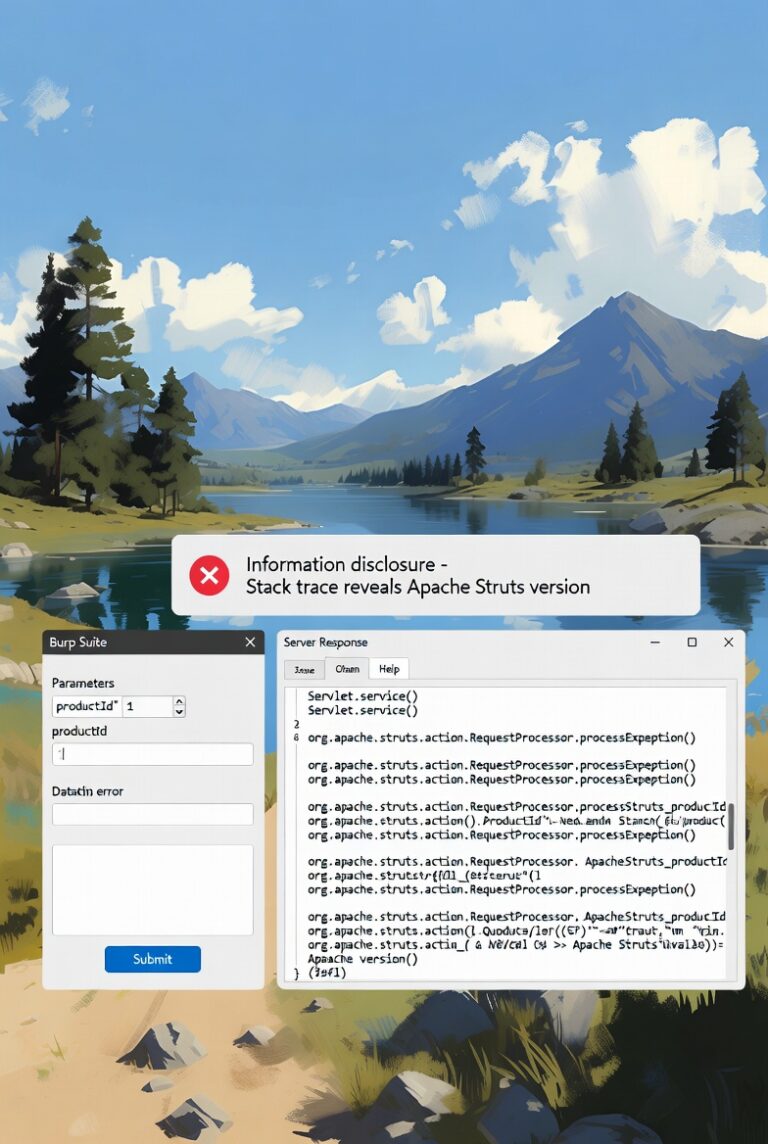
In this lab, the application is vulnerable to information disclosure through detailed…

Introduction: The Blind OS Command Injection with Out-of-Band Data Exfiltration lab from…
In the rapidly evolving landscape of information technology and cybersecurity, terminology is…
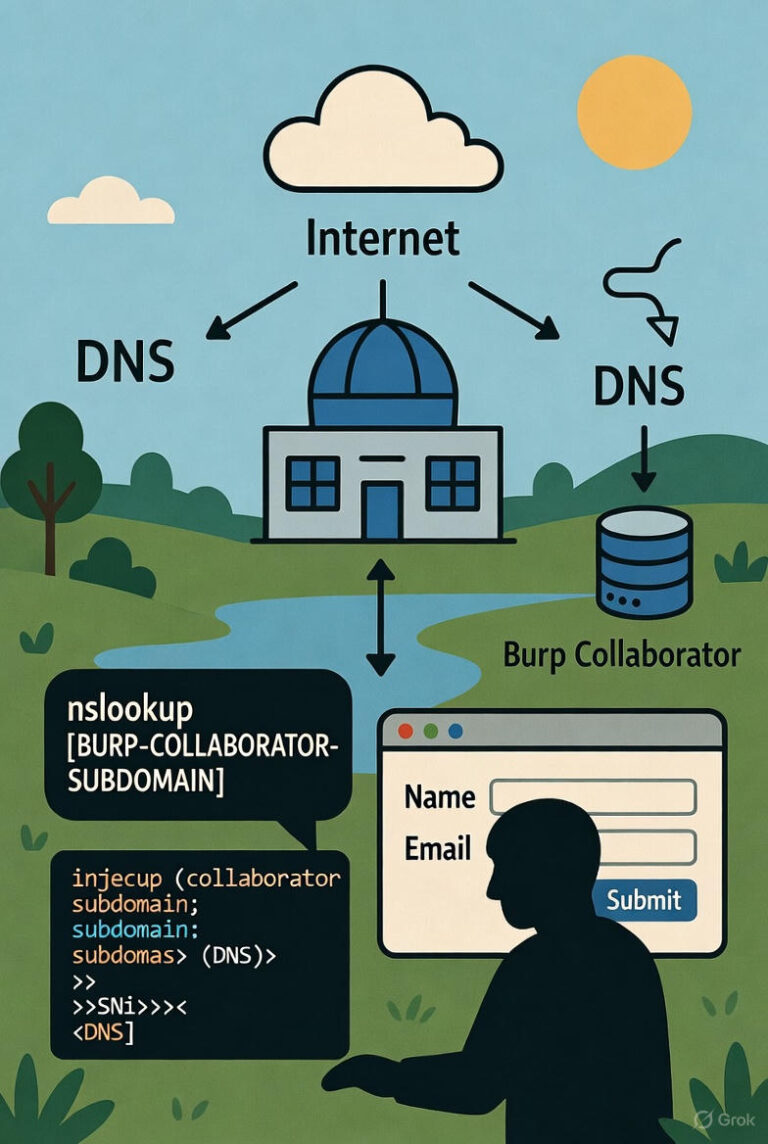
Introduction: The “Blind OS Command Injection with Out-of-Band Interaction” lab in the PortSwigger Web…