Autonomous Security Systems: The Rise of the Self-Healing Network

For decades, the goal of the Security Operations Center (SOC) was to…

For decades, the goal of the Security Operations Center (SOC) was to…

In the IT world, we are professional skeptics. We’ve seen “unhackable” systems…

We’ve all said it: “I really need to fix my privacy settings…

The narrative of cybersecurity has shifted. We are no longer just defending…
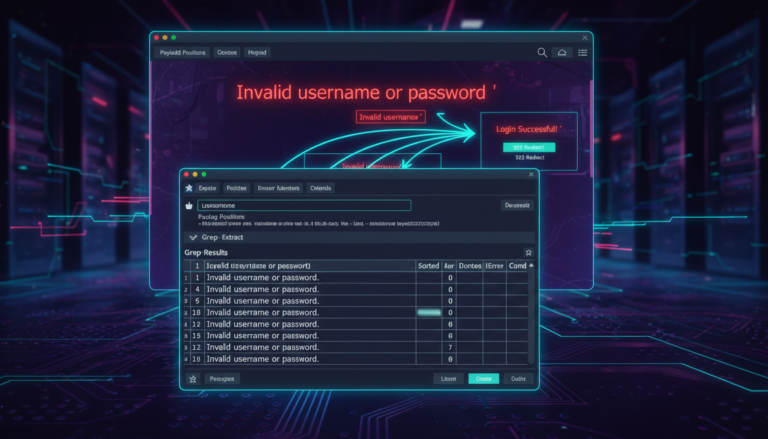
Introduction: Username enumeration vulnerabilities can manifest in increasingly sophisticated ways as developers attempt to…

We spend billions every year on the “perimeter.” We have Next-Gen Firewalls,…
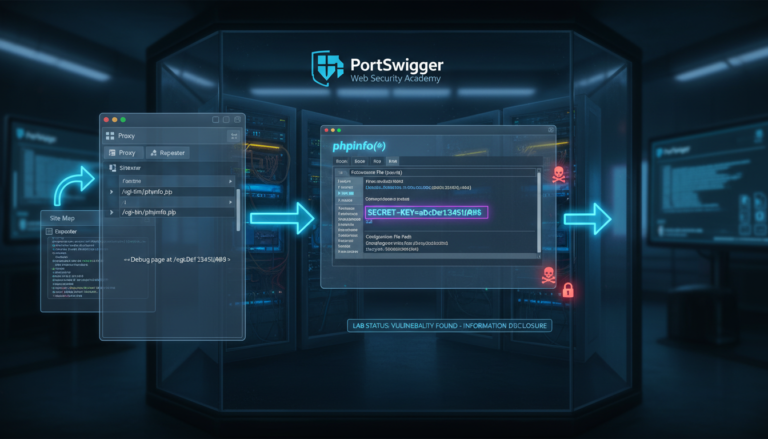
This lab demonstrates a common vulnerability where sensitive information is exposed through…