Before setting up Cybersecurity home lap, I started with exploring Operating Systems, I then went on to check the following, ensuring that my PC has the required specifications.
Hardware Requirements
- Minimum 4 GB RAM (16 GB recommended
- At least 50 GB of free disk space
- Intel/AMD processor with virtualization
- Support enabled in BIOS/UEFI
- VMware Workstation or VirtualBox (latest version)
- ISO, vmx or .ova files for Kali Linux, OWASP BWA, and Metasploitable
Download and setup vmware
- Click here to download the VMware Workstation 17 Pro installation file.
Note: The above vmware link is only for those with windows operating system.
- Click on the installation file and follow the screen instructions to install.
- Copy the activation keys below and activate your VMware player.
NZ4RR-FTK5H-H81C1-Q30QH-1V2LA
Setting Up Kali Linux
- Download Kali Linux
- Click here to visit the official Kali Linux downloads page.
- Download the pre-built virtual machine file.
- Download 7zip , Install it
- Install Kali Linux
- Open the extracted Kali in VMware
- Start the VM and log in (default credentials: kali/kali)
Update Kali Linux
- Run the following commands to update and upgrade: sudo apt update && sudo apt upgrade -y
Setting Up OWASP BWA
- Download OWASP BWA
- Click here to visit the OWASP BWA project page to download the file.
- Extract Metasploitable using 7zip
- Import OWASP BWA
- Open the extracted VM into VMware.
- Configure the network to the same host-only or NAT network as Kali Linux.
Start OWASP BWA
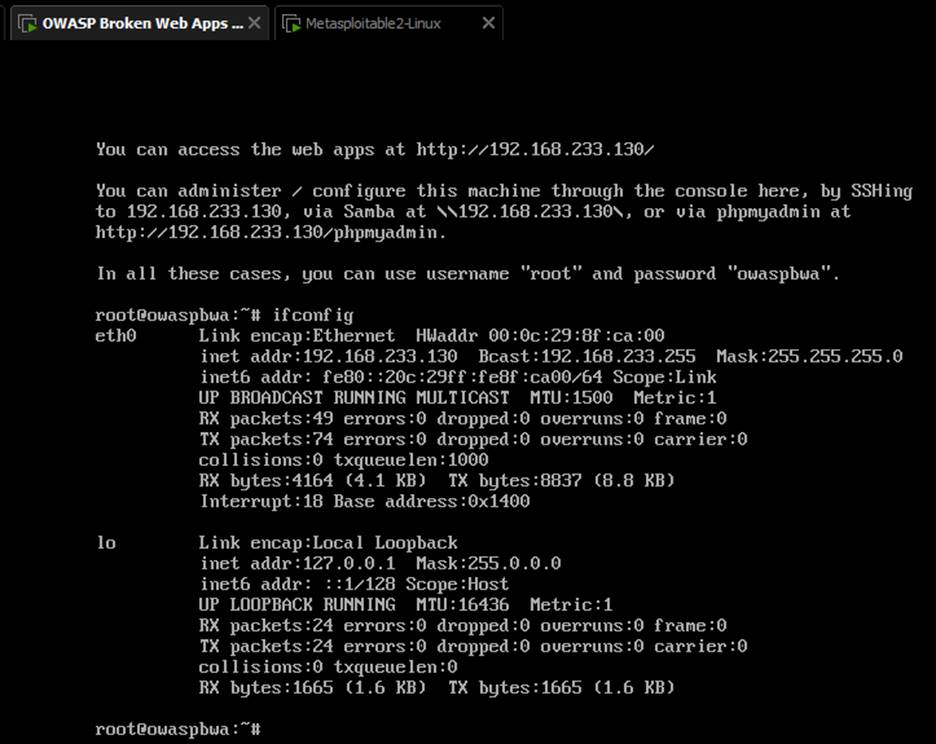
- Boot the VM and note its IP address (displayed on the console).
- Access the web applications in a browser using http://<ip_address>
Setting Up Metasploitable
- Download Metasploitable
- Download Metasploitable from Rapid7’s official site
- Extract Metasploitable using 7zip
- Import Metasploitable
- Open the extracted VM into VMware.
- Configure the network to the same host-only or NAT network as the other VMs.
Start Metasploitable
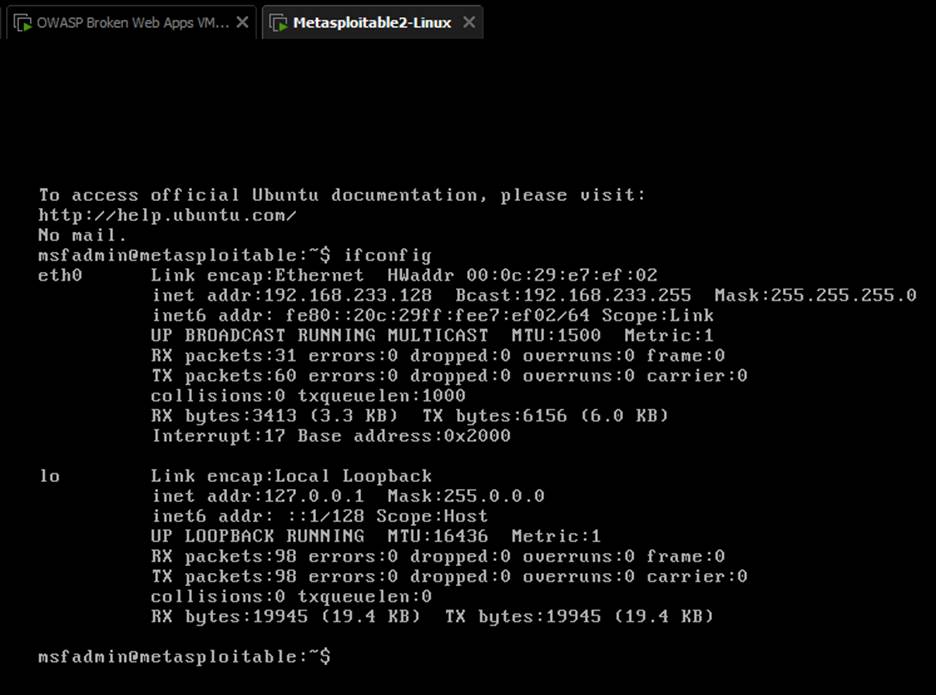
- Boot the VM and log in (Default credentials: msfadmin/msfadmin).
- Note the IP address of the VM using ifconfig
Verifying the Lab Setup
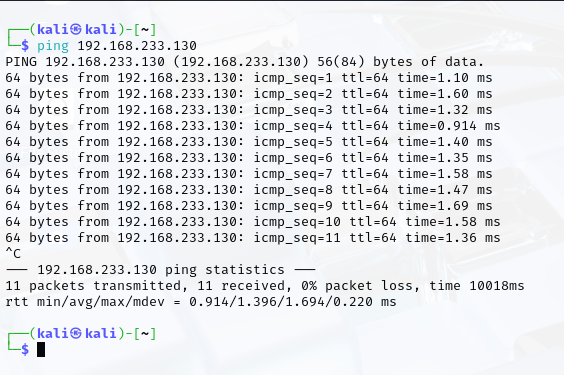
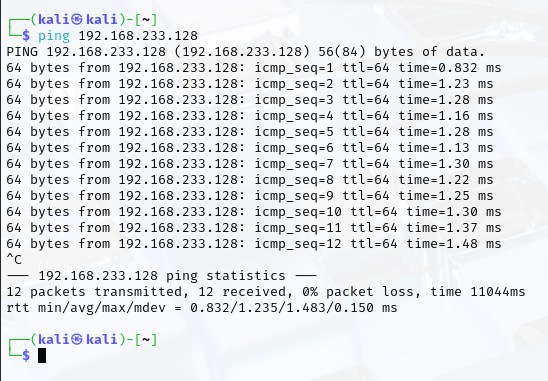
- Test Connectivity
- Ping each VM from Kali Linux to ensure network connectivity: ping <ip_address>
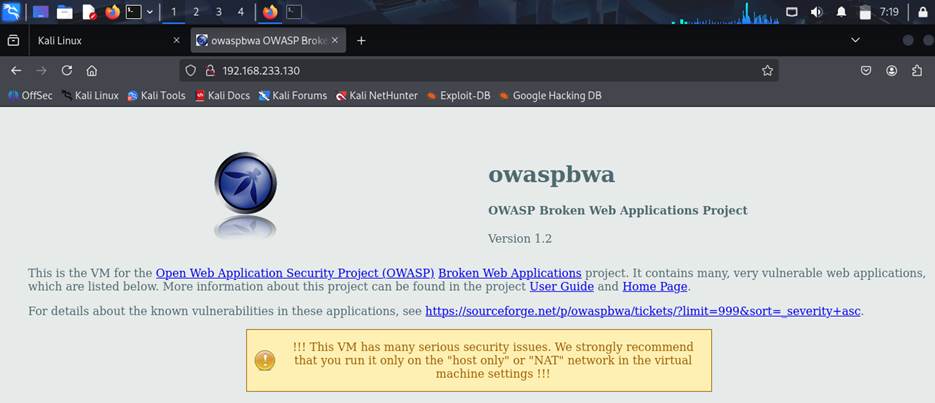
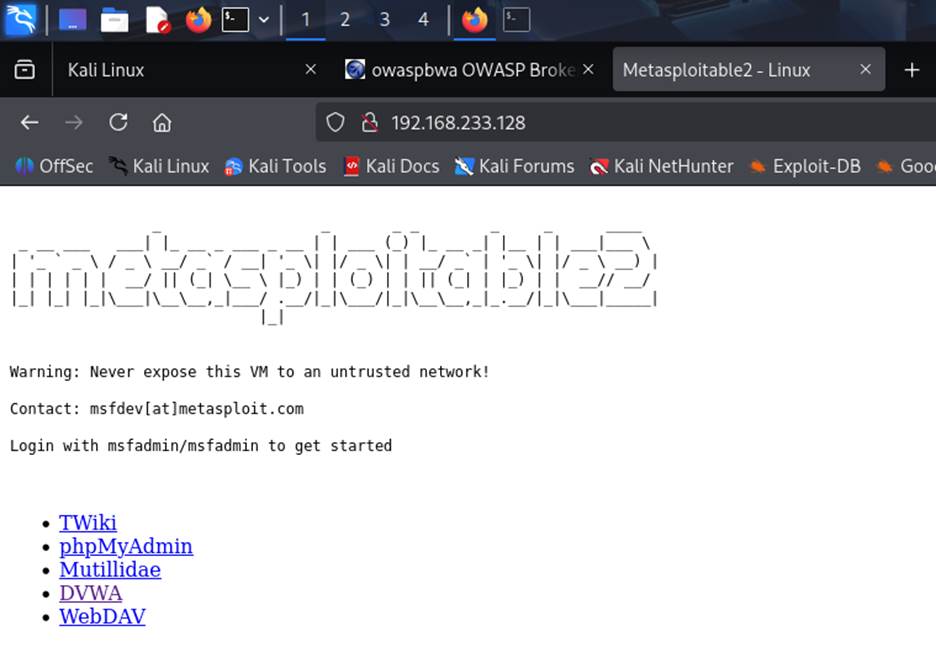
- Access Services
- From Kali Linux, use a browser or terminal to interact with OWASP BWA and Metasploitable services.
- Example: http://<owasp_bwa_iP> http://<Metasploitable>
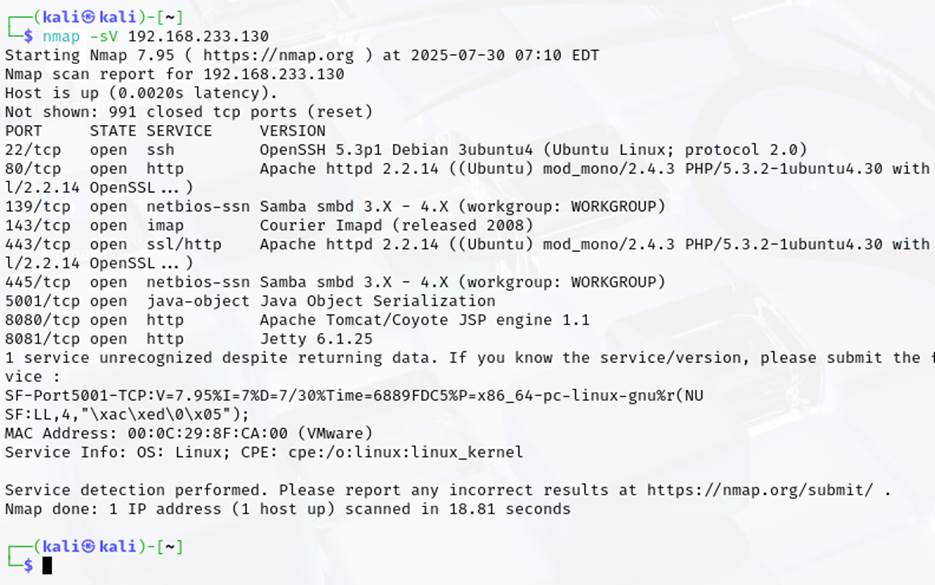
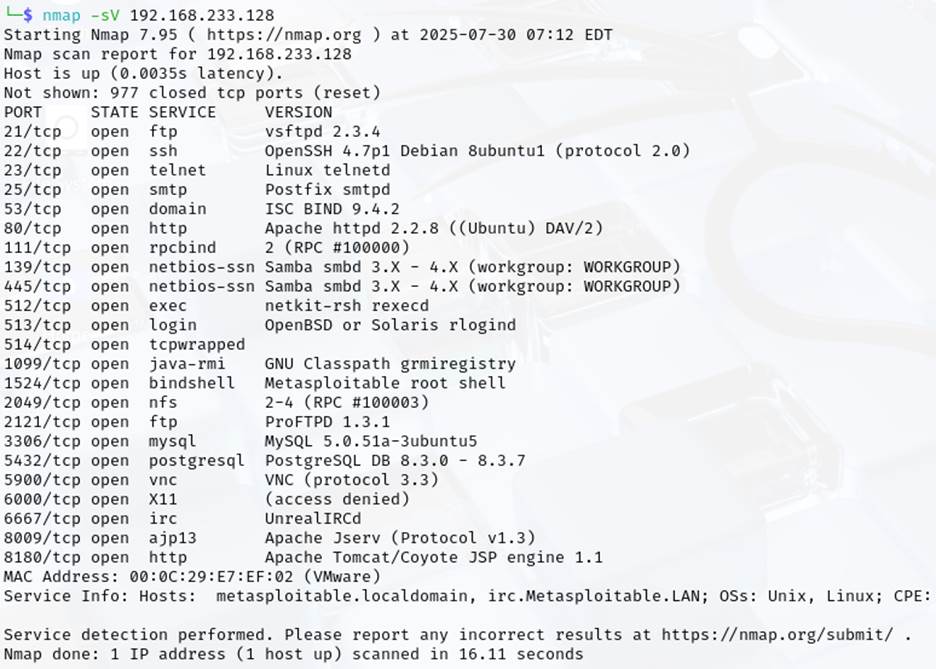
- Example: Use nmap to scan Metasploitable: nmap -sV <Metasploitable_IP>