Introduction:
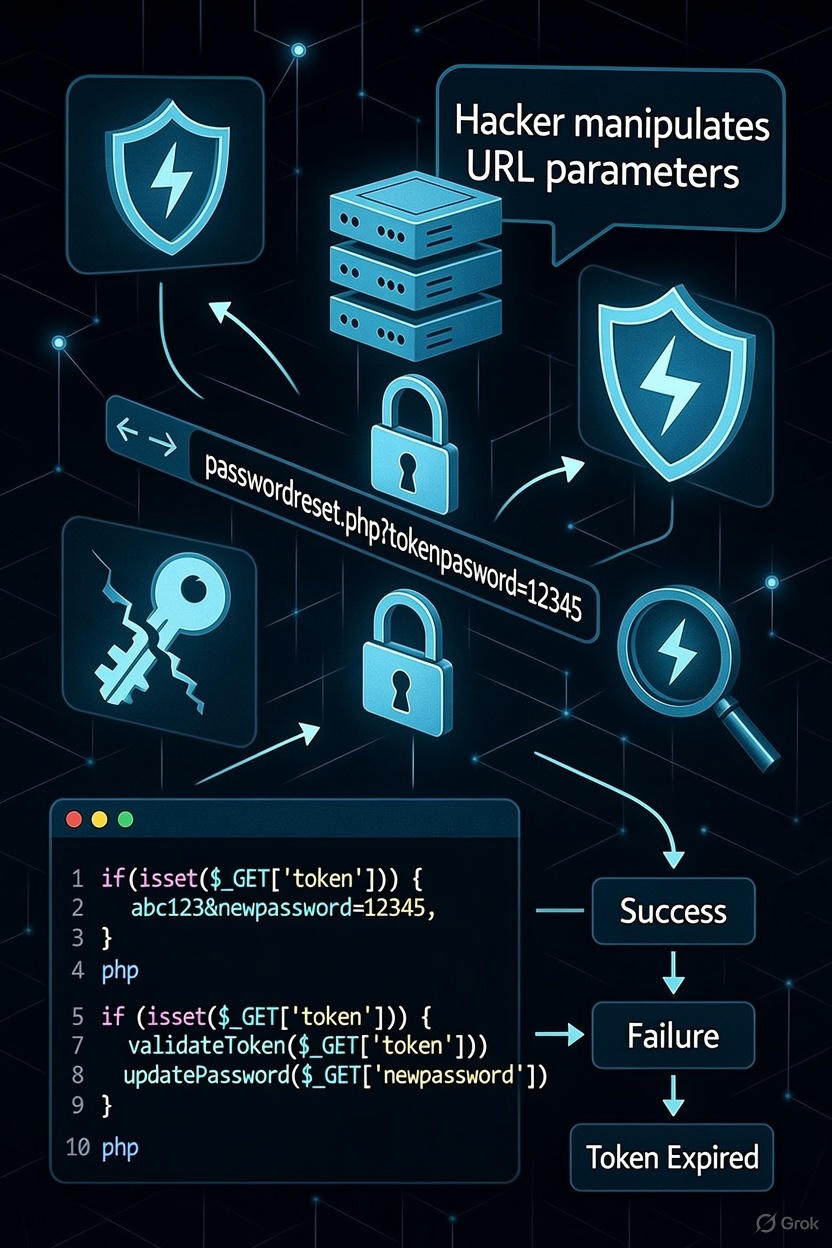
Password reset mechanisms serve as critical recovery pathways for users who have lost access to their accounts. However, flawed implementation of these systems can introduce severe vulnerabilities that allow attackers to hijack accounts without legitimate ownership. This lab demonstrates how broken password reset logic can be exploited to take control of arbitrary user accounts through token validation bypass.
Lab Setup and Objective:
The lab presents a vulnerable password reset implementation where the application fails to properly validate reset tokens during the password change process. The goal is to exploit this weakness to reset the password of a target user account (Carlos) without possessing a valid reset token, ultimately gaining unauthorized access to the account.
Detailed Walkthrough
Understanding Normal Password Reset Flow:
The process begins by initiating a legitimate password reset for one’s own account. Following the reset link sent via email and completing the password change process reveals the underlying mechanism. Analysis of the HTTP traffic shows that reset tokens are transmitted as URL query parameters, and the username is included as a hidden form field in the password submission request.
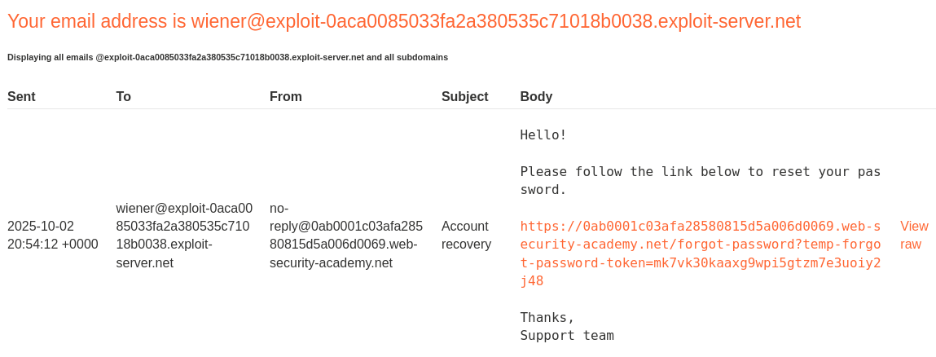
Identifying the Vulnerability:
Further examination reveals a critical flaw: the application accepts password change requests even when the reset token parameter is removed entirely from both the URL and request body. This indicates that the server is not validating the presence or correctness of the reset token during the password change operation.
Exploiting the Broken Logic:
With this vulnerability confirmed, the attack can be escalated to target Carlos’s account. A new password reset is initiated for one’s own account to generate a valid request structure. In Burp Repeater, the reset token parameters are removed, the username field is changed to “carlos,” and a new password is specified. Submitting this modified request successfully changes Carlos’s password without requiring his reset token.
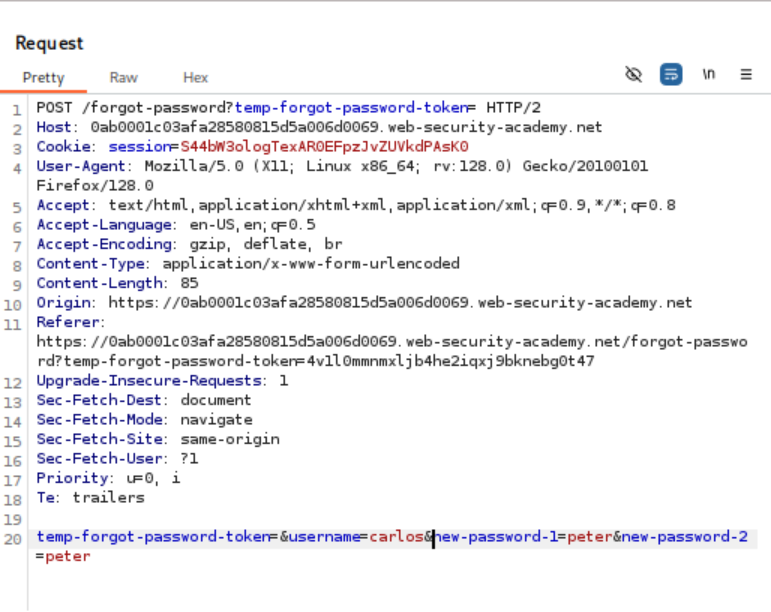
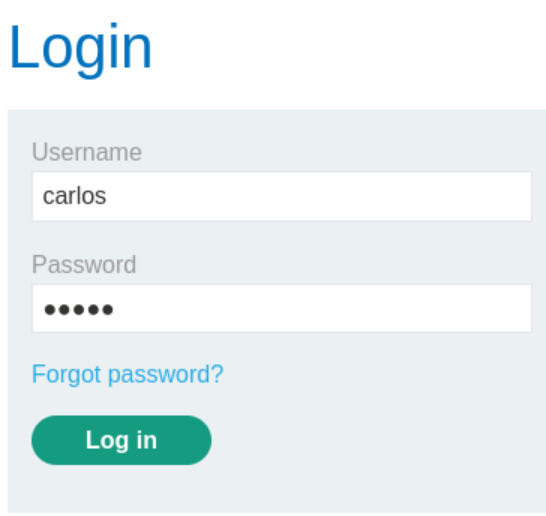
Account Takeover:
Using the newly set password, Carlos’s account can be accessed directly through the login page. Successful authentication and navigation to the account page confirms the lab completion.
Technical Insights
Vulnerability Analysis:
This vulnerability represents a classic example of broken business logic in authentication systems. The application correctly generates and sends reset tokens but fails to enforce their validation during the critical password change operation. This disconnect between token generation and enforcement creates an exploitable gap that bypasses the intended security controls.
Attack Vector Characteristics:
The primary attack vector exploits
- Inadequate server-side validation of reset tokens
- Trust in client-provided parameters without proper verification
- Disconnected security controls between token generation and enforcement
- Predictable parameter names and request structures
Mitigation Strategies:
- Robust Token Validation: Applications must validate reset tokens on both the initial reset page load and the final password submission. Tokens should be cryptographically secure, time-limited, and single-use.
- Server-Side State Management: The server should maintain state information about password reset requests, associating tokens with specific user accounts and ensuring that password changes can only occur for the account that requested the reset.
- Comprehensive Input Validation: All parameters in password reset requests should be validated server-side, including verification that the target account matches the token’s associated account.
- Token Expiration and Cleanup: Reset tokens should have short expiration times and be immediately invalidated after successful use or upon expiration.
- Rate Limiting and Monitoring: Implement rate limiting on password reset requests and monitor for suspicious patterns such as multiple reset attempts or token manipulation.
- Secure Token Storage: Tokens should be stored securely using appropriate hashing mechanisms and cleared from the database after use or expiration.
Conclusion:
This lab demonstrates how a seemingly minor oversight in password reset logic can lead to complete account compromise. The vulnerability stems from treating token validation as a formality rather than a critical security control. Organizations must implement comprehensive validation at every step of the password reset process, ensuring that security controls are consistently enforced throughout the entire workflow. Proper implementation requires treating each step as a potential attack surface and validating all assumptions about user identity and authorization.
References:
– PortSwigger Web Security Academy: [https://portswigger.net/web-security](https://portswigger.net/web-security)
– OWASP Forgot Password Cheat Sheet: [https://cheatsheetseries.owasp.org/cheatsheets/Forgot_Password_Cheat_Sheet.html](https://cheatsheetseries.owasp.org/cheatsheets/Forgot_Password_Cheat_Sheet.html)
– NIST Digital Identity Guidelines – Authentication and Lifecycle Management: [https://pages.nist.gov/800-63-3/](https://pages.nist.gov/800-63-3/)