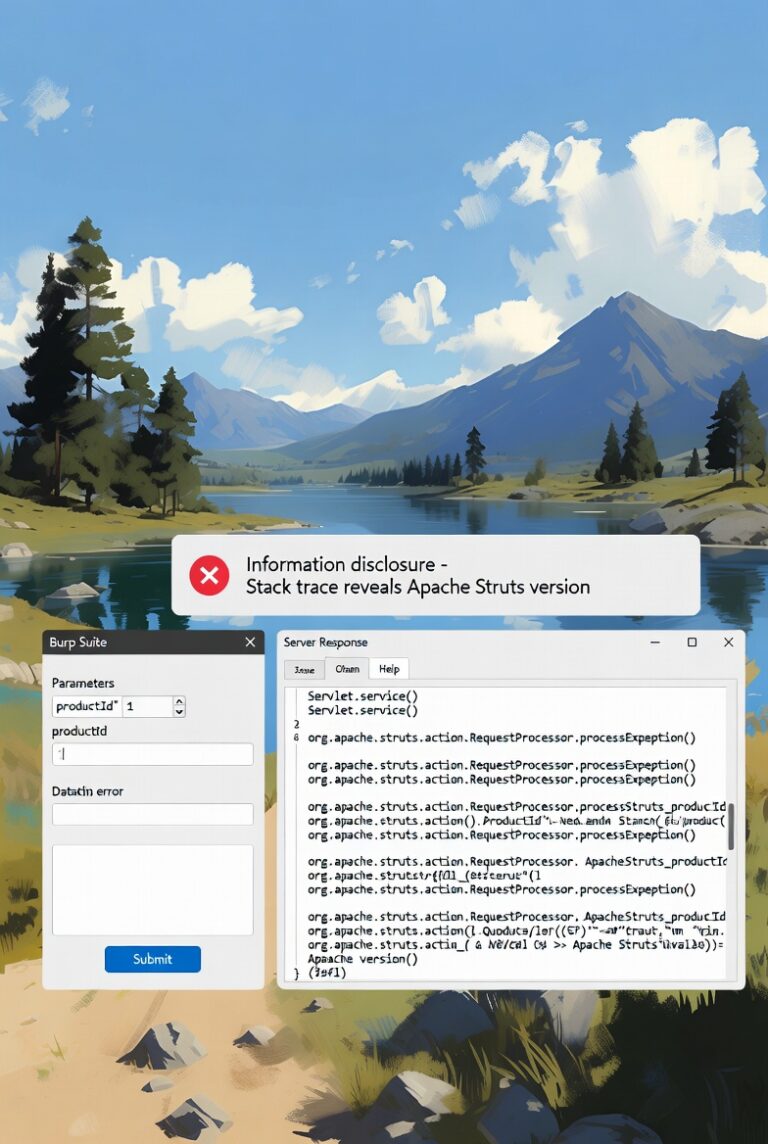
Lab: Information Disclosure on Debug Page
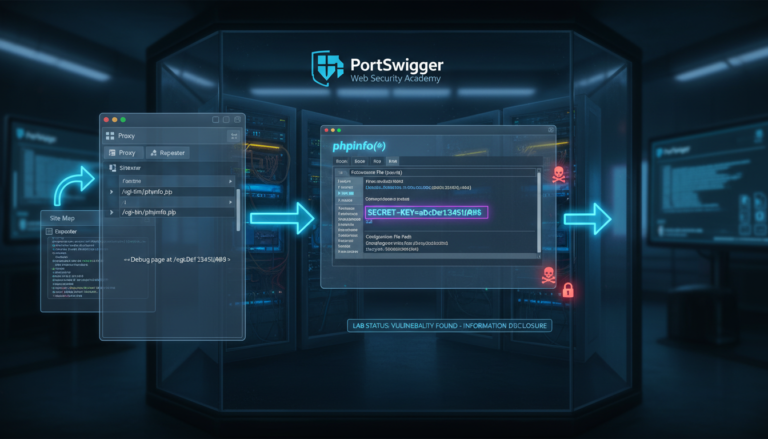
This lab demonstrates a common vulnerability where sensitive information is exposed through a debug page. Applications often include diagnostic or debugging interfaces intended for development or administrative purposes. When these pages are accessible in production environments without proper access controls, they…