Lab : Exploiting Reflected XSS in JavaScript Strings with Encoded Angle Brackets

Introduction: This lab demonstrates a Reflected Cross-Site Scripting (XSS) vulnerability where user input is…

Introduction: This lab demonstrates a Reflected Cross-Site Scripting (XSS) vulnerability where user input is…
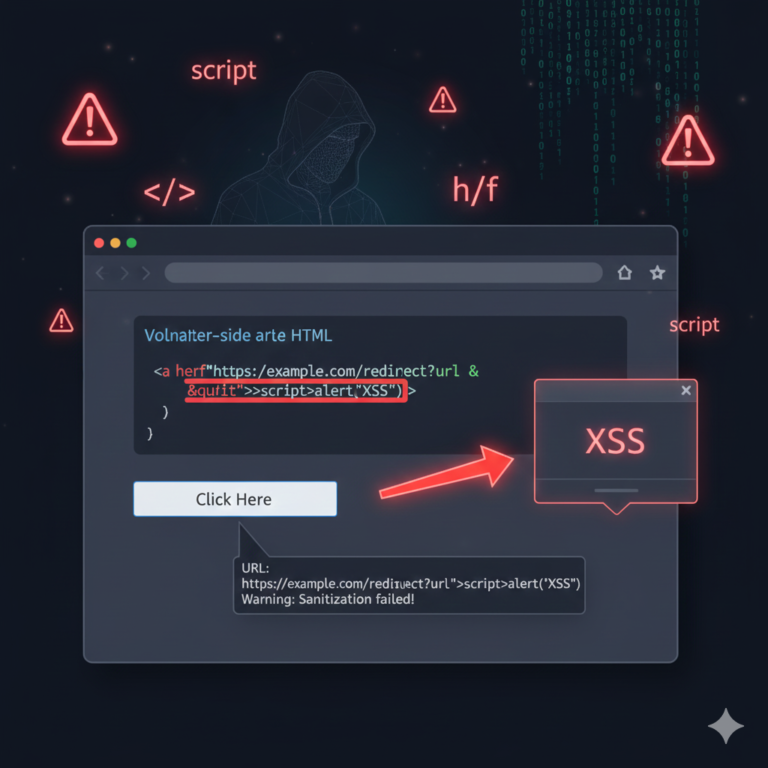
Introduction: In this post, we’ll explore a Stored Cross-Site Scripting (XSS) vulnerability where malicious…
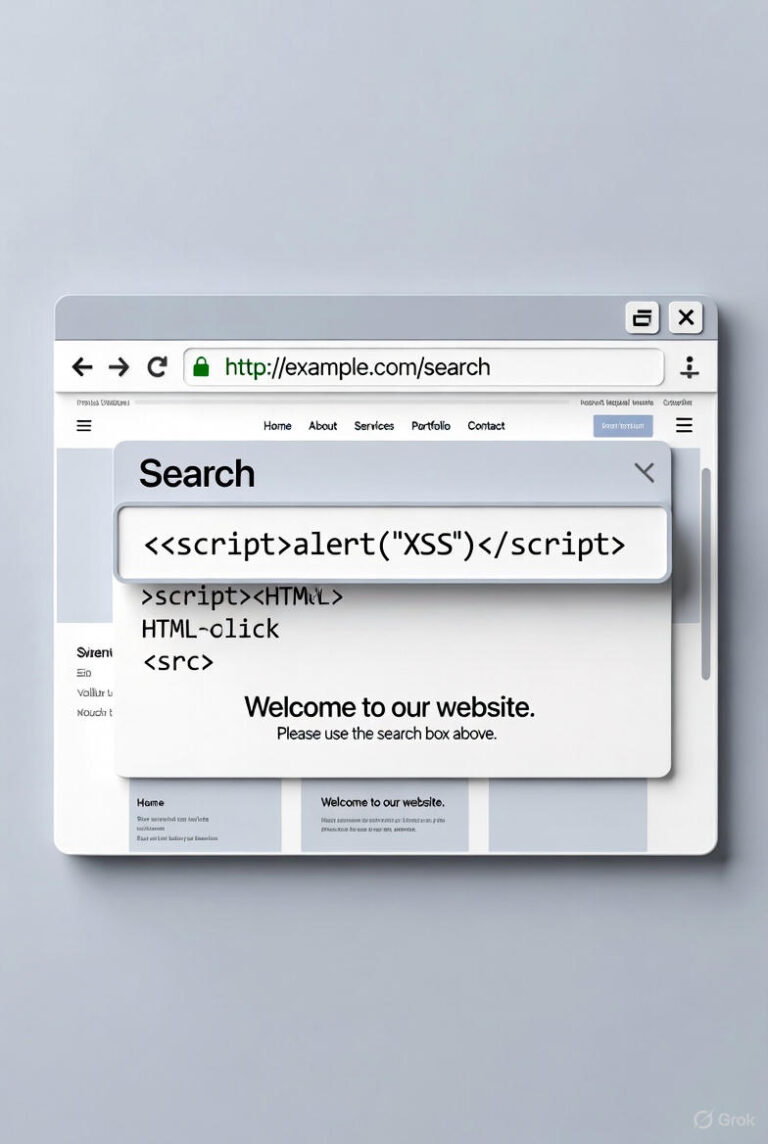
Introduction In this post, we’ll dissect a common Cross-Site Scripting (XSS) vulnerability…
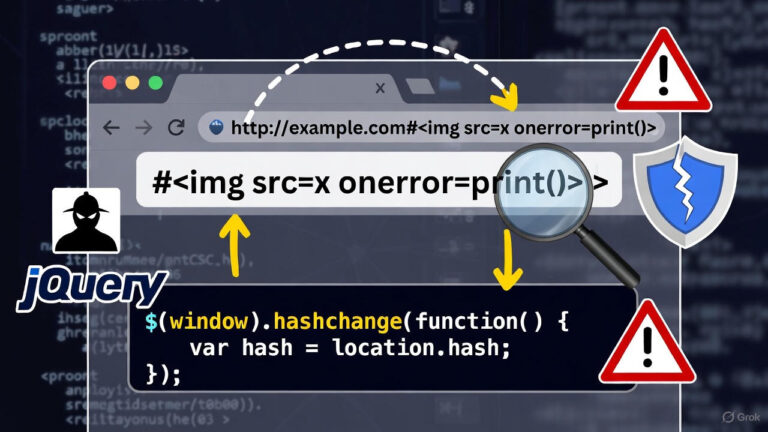
Vulnerability Type: DOM-based Cross-Site Scripting (XSS) Attack Vector The vulnerable application uses jQuery…

Introduction: In this post, we’ll explore a Stored Cross-Site Scripting (XSS) vulnerability…
Introduction In this post, we’ll dissect a common Cross-Site Scripting (XSS) vulnerability…
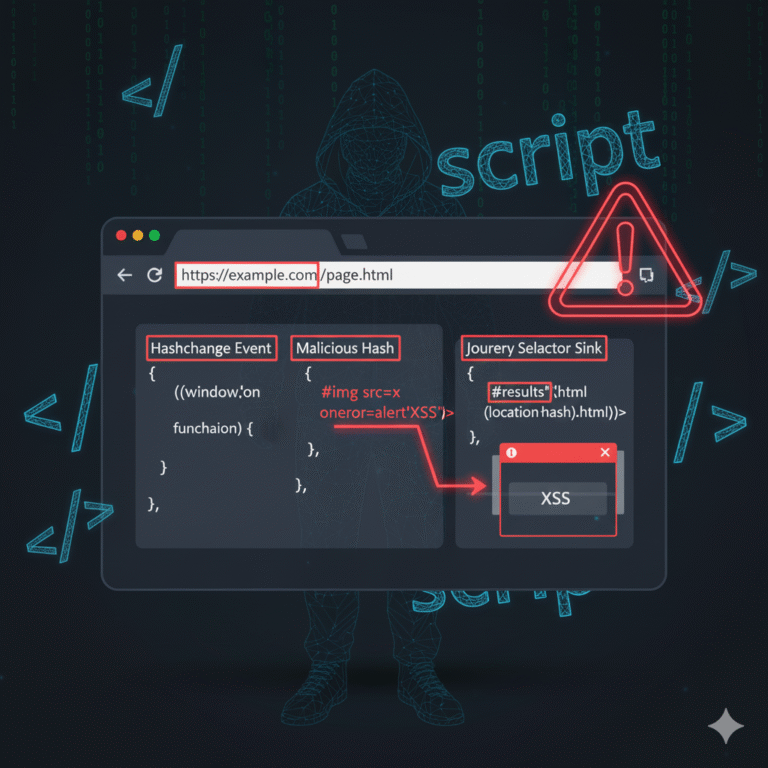
Vulnerability Type: DOM-based Cross-Site Scripting (XSS) Attack Vector The vulnerable application uses…